Acalvio Technology Advantage
Acalvio Preemptive Cybersecurity platform is built on a wide range of innovations such as: using deception to detect malicious network activities, network intrusion diversion, tunneling for deception traffic, network infrastructure obfuscation, methods for detecting and tracking adversary trajectory, threat engagement, & deception engagement, context-aware knowledge systems for deception deployment, among many others.
Acalvio is the only vendor in the deception space to have received 25+ issued patents for seminal inventions in the last five years.
The continuous innovation enables Acalvio to provide a unique feature set for ShadowPlex Identity Protection, Advanced Threat Defense and Threat Hunting products. The differentiated and robust features help enterprises in adopting an active cyber defense strategy across a diverse environment covering IT, IoT, and OT, and on-premises and cloud workloads.
The most comprehensive ”Cloud-First” Distributed Deception Platform for organizations looking to deploy Deceptions at Enterprise Scale
Efficacy
EASE OF USE
SCALABILITY
DECEPTION SECURITY
VISIBILITY
INVESTIGATE
Acalvio ShadowPlex Architecture
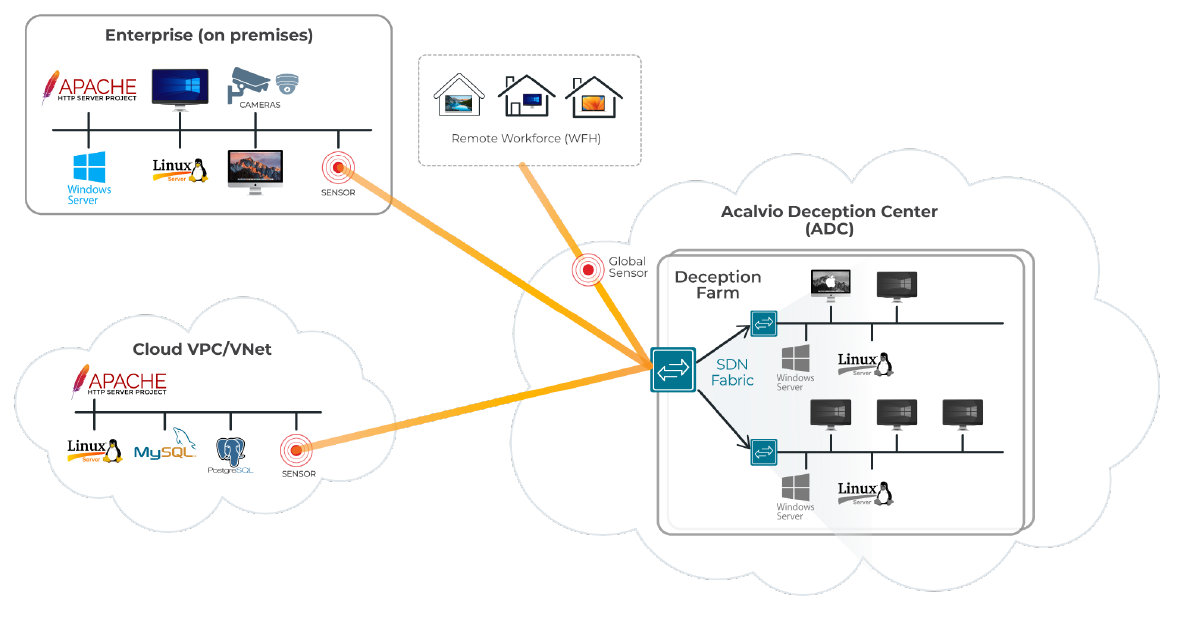

Deception Quality and Density
Traditional deception offerings are plagued with a conundrum — do you deploy lots of inexpensive low interaction decoys that provide breadth and coverage but no depth; OR a few high interaction decoys that provide depth and detail but are expensive. Through our Fluid Deception technology, ShadowPlex delivers the best of both worlds. The result is cost-effective deceptions at scale.
Autonomous Deception
- Determine deception strategy customized to every subnet
- Configure non-fingerprintable blended deception
- Generate personalized endpoint deception, unique and relevant
- Keep deception dynamic to match network changes
- Automate Alert Triage

Seminal Patented Innovations
| FEATURE: FLUID DECEPTION | Patent # | Status | ||||
| DYNAMIC SECURITY MECHANISMS FOR MIXED NETWORKS | 10,326,796 | Issued | ||||
| THREAT ENGAGEMENT AND DECEPTION ESCALATION | 10,033,762 | Issued | ||||
| NETWORK INFRASTRUCTURE OBFUSCATION |
|
Issued | ||||
| RESPONSIVE DECEPTION MECHANISMS | 10,348,763 | Issued | ||||
| FEATURE: DECEPTION PROJECTION INFRASTRUCTURE | ||||||
| NETWORK STIMULATION ENGINE |
|
Issued | ||||
| TUNNELING FOR NETWORK DECEPTIONS | 9,979,750 | Issued | ||||
| NETWORK INTRUSION DIVERSION USING A SOFTWARE DEFINED NETWORK | 10,193,924 | Issued | ||||
| DYNAMIC HIDING OF DECEPTION MECHANISM | 9,756,075 | Issued | ||||
| DECEPTION TO DETECT NETWORK SCANS | 9,985,988 | Issued | ||||
| DECEPTION MECHANISMS IN CONTAINERIZED ENVIRONMENTS | 10,972,503 | Issued | ||||
| FEATURE: AI | ||||||
| SYSTEMS AND METHODS FOR DETECTING AND TRACKING ADVERSARY TRAJECTORY | 9,961,099 | Issued | ||||
| CONTEXT-AWARE KNOWLEDGE SYSTEM AND METHODS FOR DEPLOYING DECEPTION MECHANISMS | 9,853,999 | Issued | ||||
| SYSTEMS AND METHODS FOR IDENTIFYING SIMILAR HOSTS | 9,836,512 | Issued | ||||
| FEATURE: THREAT ANALYSIS | ||||||
| USING HIGH-INTERACTION NETWORKS FOR TARGETED THREAT INTELLIGENCE | 10,230,745 | Issued | ||||
| COMMAND AND CONTROL CYBER VACCINE | 10,104,120 | Issued | ||||
| IMMUNIZING NETWORK DEVICES USING A MALWARE MARKER | 10,218,741 | Issued | ||||
| MULTIPHASE THREAT ANALYSIS AND CORRELATION ENGINE | 10,270,789 | Issued | ||||
| ENTERPRISE DNS ANALYSIS | 10,362,057 | Issued | ||||
| TESTING ENVIRONMENT CYBER VACCINE | 10,419,479 | Issued | ||||
| FEATURE: HONEY REDIRECTION | ||||||
| ALTERNATE FILES RETURNED FOR SUSPICIOUS PROCESSES IN A COMPROMISED COMPUTER NETWORK |
|
Issued |
Next Steps
Explore our patented technologies to enable Preemptive Cybersecurity and Identity Protection in your enterprise.