
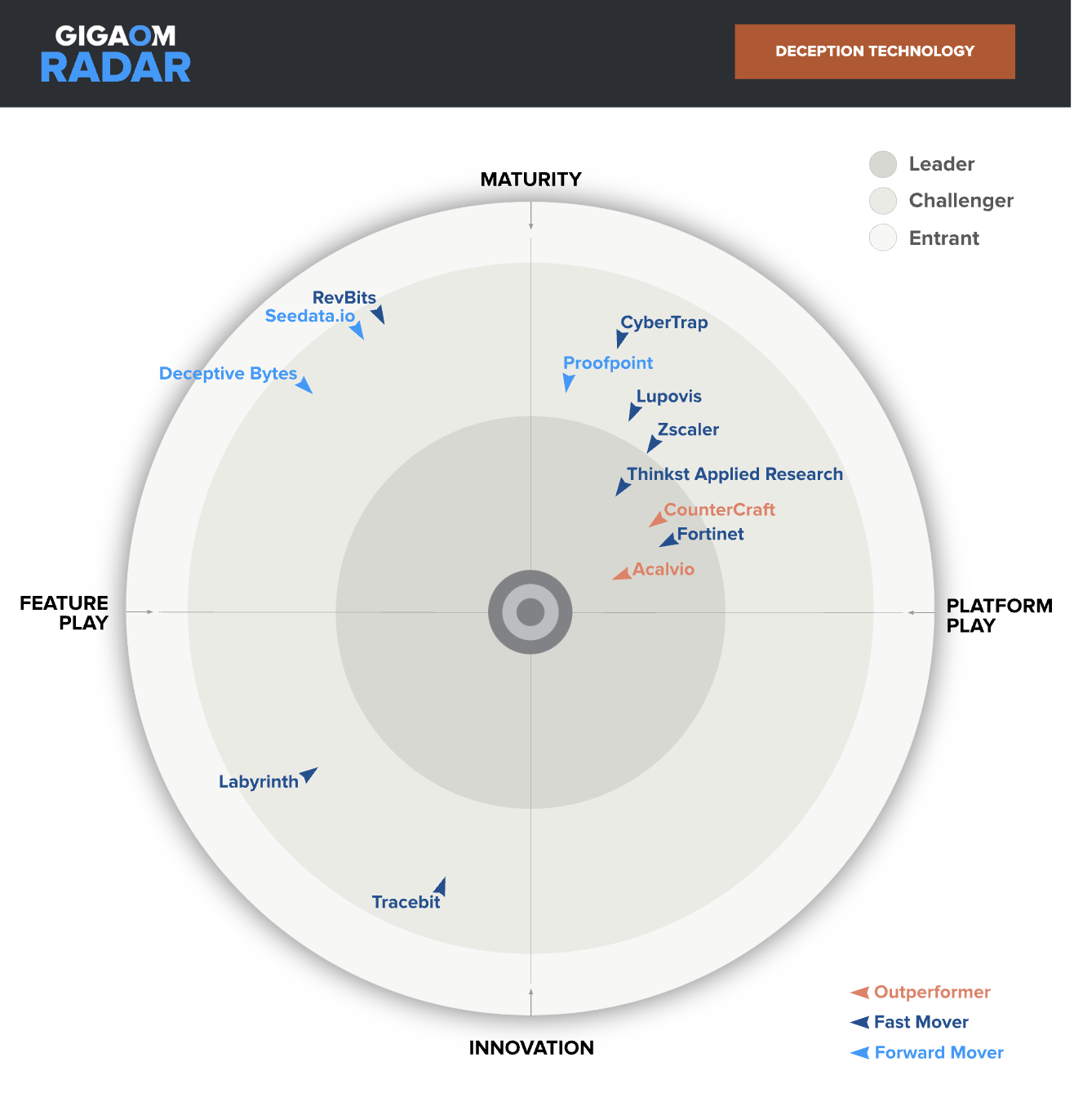
 Figure 1: Acalvio continues its industry leadership in deception (closest to the inner circle)
Figure 1: Acalvio continues its industry leadership in deception (closest to the inner circle)Why AI-driven attacks are driving a paradigm shift to proactive defense
The threat landscape has changed radically with the advances in AI and LLMs. Attackers are increasingly leveraging LLMs to identify novel one-day and zero day vulnerability exploits and generate polymorphic malware variants. LLMs are rapidly gaining the capability to convert natural language prompts into offensive tooling, resulting in an explosion of attacker tools and techniques. In addition, LLMs are able to analyze and interpret complex relationships between enterprise resources, for example, to find attack pathways leading to high-value assets by analyzing the users, computers, and groups in Active Directory.
The evolving threat landscape is driving a paradigm shift in security, with traditional reactive approaches that require a priori knowledge of the threat being less effective against modern, AI-driven threats. Security teams are increasingly adopting a proactive approach to threat detection, one that is based on anticipating the threat and ensures coverage as the attacker methods evolve.
Cyber deception is foundational for modern proactive security. The advances in AI are resulting in a shift from reactive approaches to proactive and preemptive approaches that anticipate threats and can detect evolving threats with novel attacker techniques.
Acalvio ShadowPlex: industry-leading deception with unmatched scalability and ease of use
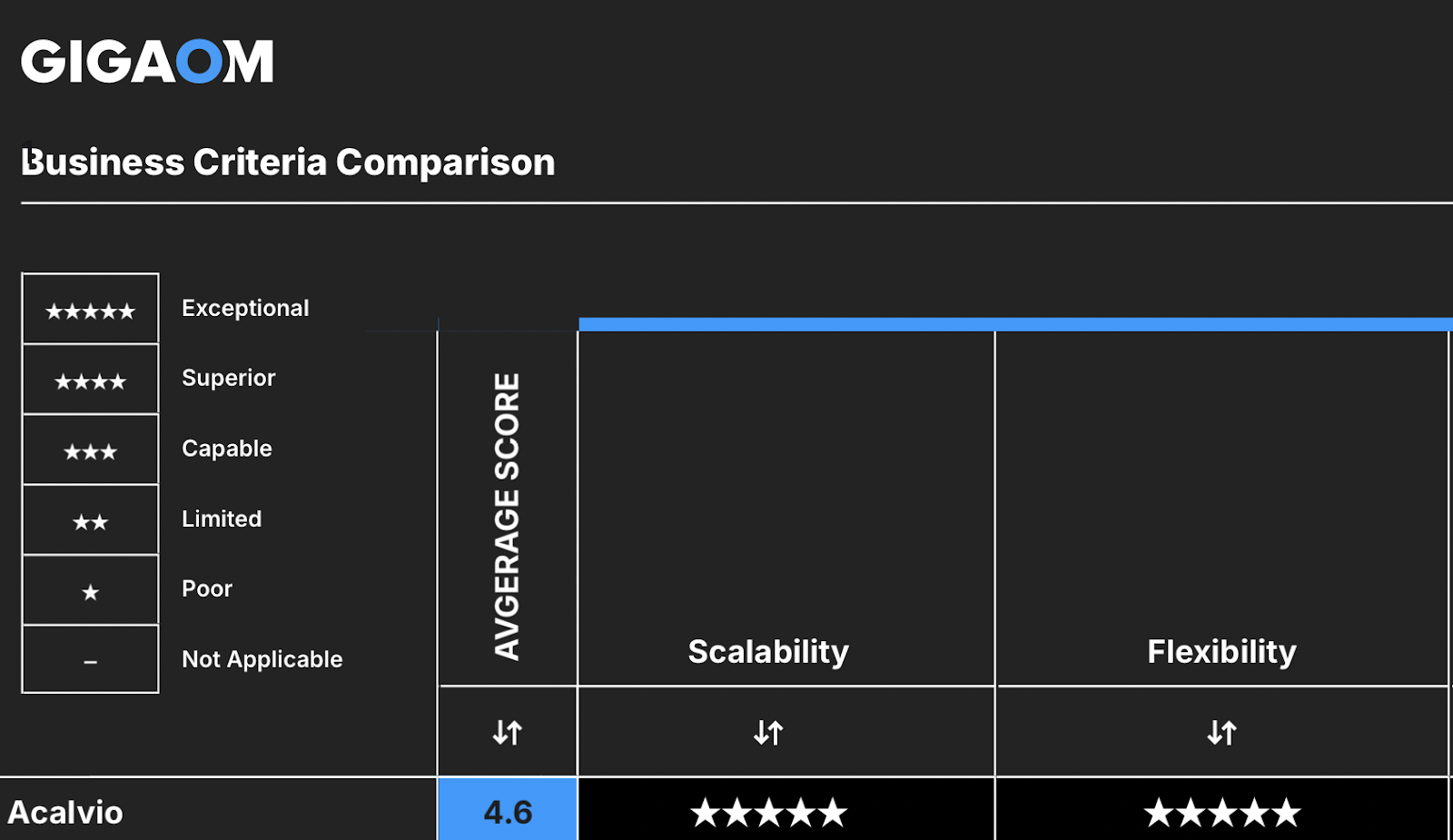 Figure 2: Acalvio’s solution given 5 out of 5 for unmatched scalability and flexibility
Figure 2: Acalvio’s solution given 5 out of 5 for unmatched scalability and flexibilityAcalvio’s technology differentiation and robust deception capabilities backed by AI are the key constituents that are underpinning the industry leadership in cyber deception. Acalvio’s platform is backed by significant intellectual property, with over 25 issued patents in cyber deception.
ShadowPlex is a comprehensive deception solution that operates as a standalone product. It deploys and manages decoys across cloud, on-premises, and hybrid environments to detect adversary presence and activities. From a scalability perspective, Acalvio’s architecture allows for deployment flexibility across diverse environments. Their fluid deception technology extends the effectiveness of decoys by modulating behaviors, which reduces maintenance requirements and operational overhead.
An intuitive interface, including role-based views and guided configuration wizards, reduces implementation complexity. The solution’s “reflection” approach to deception deployment enables broad coverage across various technology environments while maintaining operational simplicity.
Acalvio was classified as an Outperformer given its ability to continuously improve on existing features, expand its feature set, and rapidly develop new services, demonstrating significant market momentum and innovation potential.
Use case: identity deception
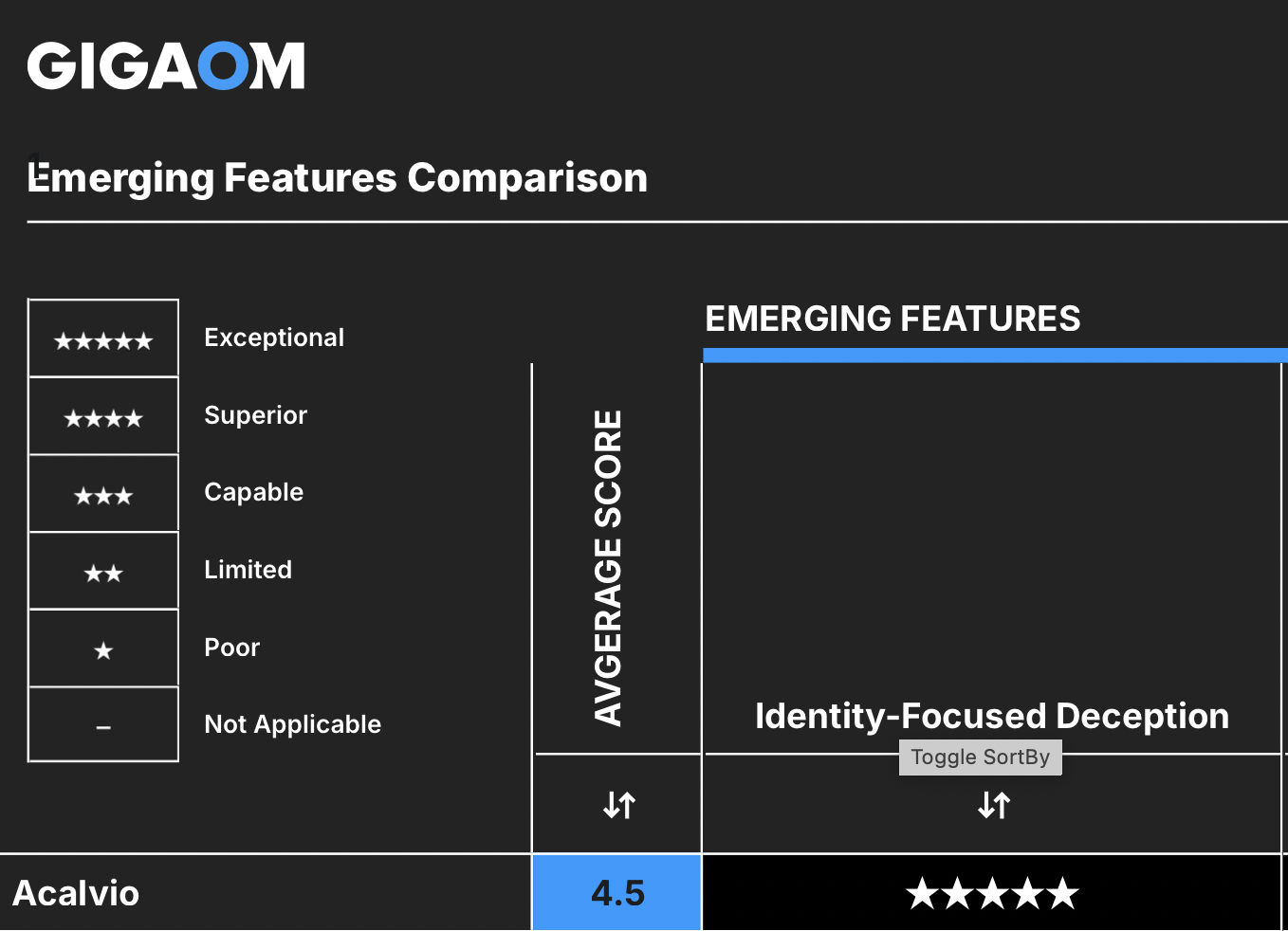 Figure 3: Acalvio scores maximum rating for identity-deception
Figure 3: Acalvio scores maximum rating for identity-deceptionIdentity-driven attacks are escalating, as adversaries leverage valid credentials for lateral movement. The recent guidance from the NSA and Five Eyes security agencies identifies the challenges with detecting attacks targeting Active Directory (AD), with malicious activity looking identical to normal usage. The guidance highlights the need and importance of honeytokens as an effective approach to protect AD.
Acalvio has robust identity deception capabilities, with native integrations with CrowdStrike, Microsoft, and Palo Alto for enterprise-scale honeytokens for identity defense. Acalvio leverages AI to automate the configuration and placement of honeytokens (deceptive user accounts and service accounts) in identity stores and on endpoints (deceptive credential profiles). The GigaOm research identifies identity deception as one of the key use cases where Acalvio provides industry leading capabilities.
Identity defense represents a standout use case where Acalvio detects unauthorized access attempts through strategically placed deception assets that monitor both cloud and on-premises identity systems. The solution’s ability to deploy fluid deception across multiple identity providers while integrating with existing identity and access management (IAM) infrastructure makes it particularly effective for organizations concerned with credential theft and privilege escalation.
Use case: cloud deception
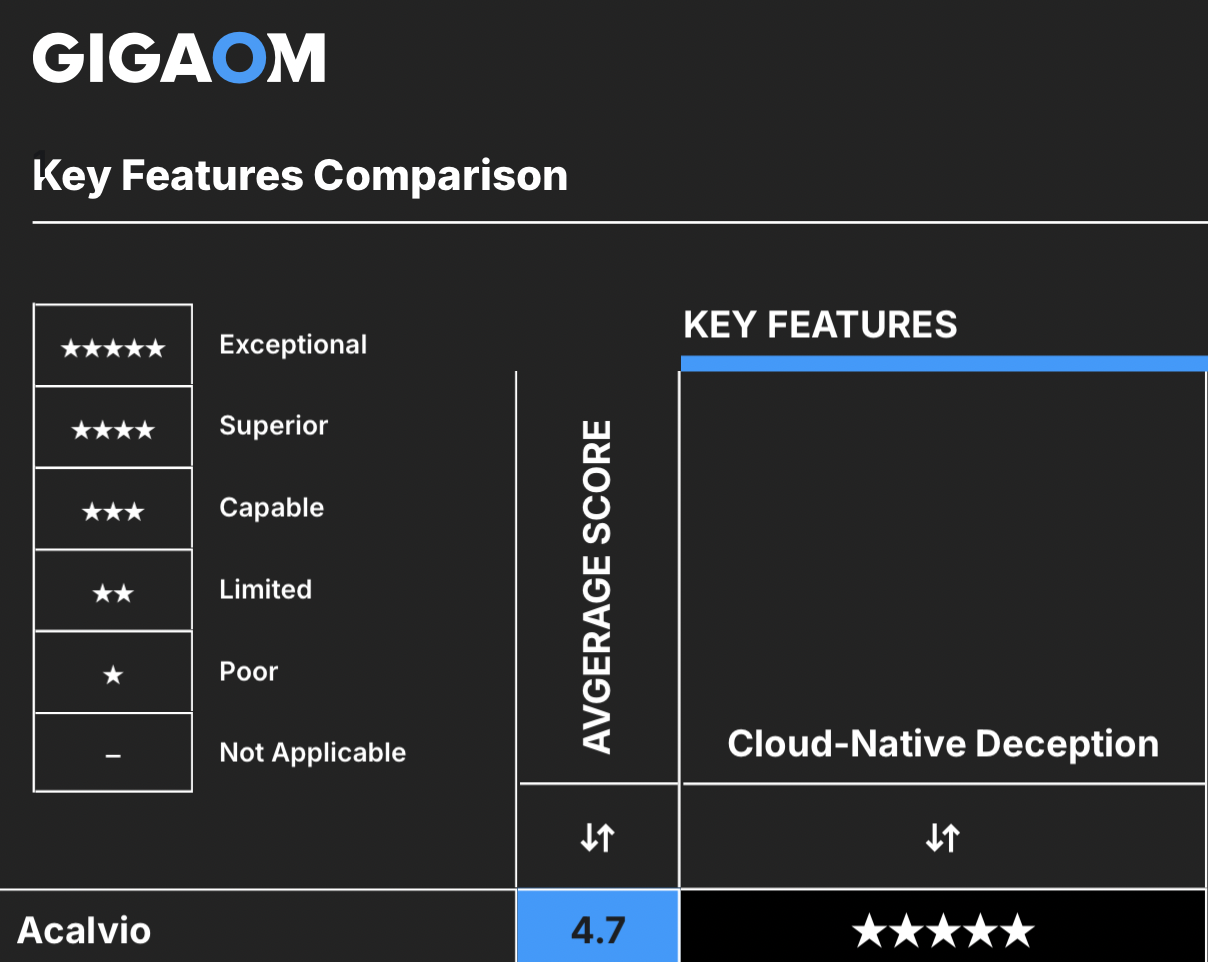 Figure 4: Acalvio’s cloud deception gets highest ratings
Figure 4: Acalvio’s cloud deception gets highest ratingsAttackers are pivoting to cloud environments, with modern threats leveraging built-in cloud primitives for privilege escalation and lateral movement. These attacks, known as Living off the Cloud (LOTC) attacks, are highly challenging to detect.
Cloud security has traditionally focused on prevention measures, with cloud security posture management solutions. The ever-expanding set of cloud services, the expanding set of actions allowed in the cloud are resulting in the need for threat detection in the cloud.
Honeytokens serve as an effective approach for threat detection in the cloud. Honeytokens provide early warning of cloud threats and protect cloud-native workloads, including Kubernetes orchestrated environments and serverless workloads. Acalvio’s cloud honeytoken offerings protect multi-cloud workloads through the strategic placement of account honeytokens (deceptive IAM users, roles, policies) and workload honeytokens (deceptive access keys and secrets). The deployment is agentless, eliminating the need for privileged access to the cloud environment.
Cloud-native security operations benefit from Acalvio’s ability to adapt deception assets automatically as cloud environments change. The solution’s integration with major cloud providers and ability to protect containerized workloads helps security teams maintain visibility across dynamic cloud infrastructure without requiring constant reconfiguration of deception elements.
Read the 2025 GigaOm Radar report for Deception Technology to learn more about GigaOm’s assessment of Acalvio’s ShadoPlex platform for deception technology and how it compares with other deception technology solutions.


