
Summary
A large enterprise faced a critical insider threat when a rogue administrator exploited a service account and script used for managing user accounts in Active Directory (AD). The attacker attempted to disable user accounts, including an Acalvio honeytoken account strategically placed to attract unauthorized access. This triggered an immediate, high-fidelity alert that enabled the SOC team to identify and stop the attack before it caused significant disruption. The organization avoided a major outage, underscoring the power of deception technology to stop real-world threats undetected by traditional security solutions.
Anatomy of the attack
The identity provisioning team utilized a service account to automate the creation and deactivation of user accounts in Active Directory (AD). The credentials for this service account were securely managed through a Privileged Access Management (PAM) solution.
However, the insider, leveraging their trusted access to the environment, exploited a critical vulnerability. They gained access to a server hosting a script designed for account provisioning and deprovisioning. This script operated under the service account’s permissions. By checking out the service account credentials from the PAM solution, the insider was able to execute the script. They then began systematically updating and disabling user accounts in AD.
Early in this malicious activity, the insider targeted an Acalvio honeytoken account—a deceptive asset deliberately placed in AD to resemble a privileged administrator account. This interaction with the honeytoken immediately triggered a high-fidelity alert, signaling the SOC team.
Despite the organization’s layered security defenses—including PAM for policy enforcement, Endpoint Detection and Response (EDR), and anomaly-based AD monitoring—none of these controls detected the attack. The deception alert was the only signal of compromise, as the insider’s actions appeared legitimate through traditional detection lenses.
The SOC team promptly investigated the alert, traced it to the server where the script was executed, identified the malicious insider, and revoked their access. This swift response halted the attack before it could escalate. If left unchecked, the insider could have disabled critical accounts, such as those belonging to executive leadership, privileged administrators, and essential services—potentially leading to a crippling organizational outage.
Why existing security controls failed
The organization had invested heavily in security controls, including PAM for prevention and policy enforcement, EDR for endpoint detection and response, and anomaly and rule-based detection at the Domain Controller (AD). Despite these measures, the insider attack bypassed all existing defense layers without triggering a single alert.
The root cause of this failure lies in the design of traditional security controls, which focus on detecting “known bad” behavior. These systems rely on attacker Tactics, Techniques, and Procedures (TTPs) as the basis for detection. This TTP-centric approach assumes that malicious activity will exhibit recognizable patterns or anomalies associated with prior attacks.
However, a malicious insider with legitimate access to enterprise resources operates within the bounds of normal workflows. In this case, the insider accessed a provisioning script, leveraging valid permissions and a trusted service account to disable user accounts in AD. From the perspective of traditional security solutions, the insider’s actions appeared indistinguishable from routine account deprovisioning activities. The logs and network traffic generated mirrored legitimate workflows, effectively evading detection.
Modern threat actors, both external and internal, understand these limitations and continuously adapt their techniques to exploit them. This incident illustrates not only the sophistication of modern adversaries but also the inherent gaps in traditional defenses. It highlights the critical need for complementary detection mechanisms, such as deception, that operate independently of attacker TTPs and can uncover malicious intent hidden within seemingly legitimate activity.
Why this attack could have had significant consequences
Active Directory (AD) is the backbone of enterprise authentication and authorization, underpinning nearly every critical function in the organization. Its proper functioning and the integrity of its data are essential to maintaining operational continuity. Any disruption to AD can result in immediate and severe consequences.
In this incident, the malicious insider possessed the necessary privileges to disable all user accounts in AD. Had the attack progressed, the insider could have disabled accounts critical to the organization’s operations, including:
- Executive leadership accounts, affecting strategic decision-making and communication.
- Domain administrator accounts, crippling IT’s ability to manage and restore systems.
- Service accounts essential for running critical applications and business processes.
The consequences of such an attack would have been catastrophic, leading to an enterprise-wide outage. Beyond operational paralysis, the organization would likely face significant financial losses, reputational damage, and potential legal ramifications due to service disruptions and compromised data integrity.
Adding to the urgency, the rapid evolution of AI technology has made it easier for adversaries to craft sophisticated attack tools and exploit novel vulnerabilities, such as zero-day exploits. As the frequency and complexity of cyber threats continue to escalate, traditional security controls alone are insufficient. It is imperative for organizations to implement advanced defenses that operate independently of attacker Tactics, Techniques, and Procedures (TTPs), such as cyber deception, to detect and mitigate evolving threats that bypass conventional systems.
Why cyber deception is a necessary control for threat detection
Cyber deception is a proactive security approach that involves deploying decoy assets to lure attackers and monitoring any interaction with these traps. Unlike traditional controls, deception assets are not part of legitimate IT or business workflows, making any engagement with them an unequivocal indicator of malicious intent.
What sets deception apart is its focus on attacker goals rather than specific tactics or techniques. By understanding the objectives of an attacker—such as gaining access to privileged accounts or disrupting operations—deception strategically positions traps to align with these goals.
While attacker Tactics, Techniques, and Procedures (TTPs) constantly evolve, their fundamental objectives remain consistent. In an Active Directory (AD) environment, for instance, attackers may aim to escalate privileges, gain unauthorized access to sensitive resources, or cause widespread disruption. Deception exploits this predictability, providing a layer of detection that is independent of specific attack methods.
An effective deception strategy involves carefully selecting the type, quantity, and placement of traps to maximize their likelihood of engagement. Acalvio’s deception platform leverages AI to automate this process, ensuring traps are not only strategically placed but also contextually relevant to the attacker’s objectives. In this instance, honeytoken accounts mimicking privileged AD users served as compelling targets. When the malicious insider interacted with one of these honeytokens, it triggered an immediate, high-fidelity alert.
This alert enabled the SOC team to swiftly investigate and neutralize the threat, stopping the insider before significant damage could occur. By offering detection that is agnostic to attacker TTPs, deception provided an essential layer of defense, safeguarding the organization against a potentially crippling outage.
Defense in depth for identity protection
Modern attackers increasingly target identity architectures, seeking to escalate privileges, access sensitive resources, or disrupt operations. Defending against these threats requires a multi-layered approach that integrates preventive, detective, and responsive controls.
An effective defense-in-depth strategy begins with identity-centric preventive measures, such as Identity and Access Management (IAM), Privileged Access Management (PAM), and Identity Governance and Administration (IGA), to enforce policies and minimize the risk of unauthorized access. Multifactor Authentication (MFA) further strengthens this layer, ensuring that access requests are validated with additional security checks.
However, preventive measures alone are insufficient. Attackers often exploit legitimate workflows or trusted credentials, bypassing these controls. This is where detection-focused solutions, like deception technology, play a critical role. By deploying decoy accounts and assets, such as honeytokens, deception creates a trap for attackers attempting to manipulate identity systems. Interactions with these traps trigger immediate, high-fidelity alerts, as shown in the central panel of the diagram, enabling swift investigation and incident response.
The final layer focuses on response actions, such as resetting compromised credentials, disabling affected accounts, or requiring step-up authentication to mitigate ongoing threats. Together, these actions contain the attack and prevent further damage.
The integration of these complementary layers—prevention, detection, and response—creates comprehensive coverage and reduces the risk of security gaps. By combining traditional controls that focus on “known bad” with deception that is agnostic to attacker Tactics, Techniques, and Procedures (TTPs), organizations can effectively address both current and emerging threats. This layered approach strengthens the overall identity protection strategy and enhances resilience against sophisticated adversaries.
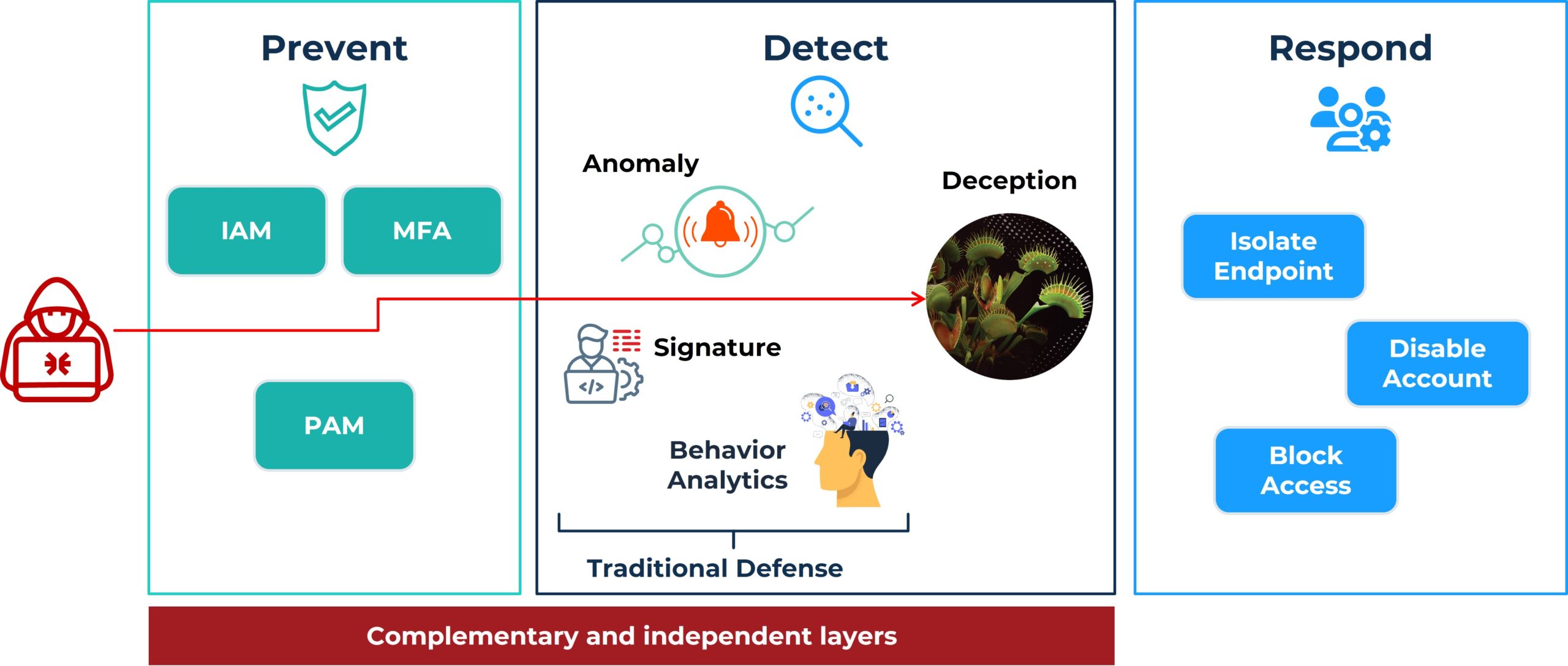
Defense in Depth for Identity Protection
Summary
This real-world case underscores the critical role of deception technology in defending against advanced threats, including insider attacks that bypass traditional security controls. At a large enterprise, a rogue administrator exploited legitimate workflows, leveraging trusted credentials to disable user accounts in Active Directory (AD). Despite the presence of robust security controls—such as Privileged Access Management (PAM), Endpoint Detection and Response (EDR), and anomaly-based monitoring—these tools failed to detect the attack.
Acalvio’s cyber deception platform, however, proved invaluable. By deploying strategically placed honeytoken accounts designed to attract unauthorized access, the organization detected the malicious activity early and triggered an immediate, high-fidelity alert. This enabled the SOC team to investigate and neutralize the insider, preventing a potentially catastrophic outage that could have disrupted critical operations and caused significant financial and reputational damage.
The incident highlights the limitations of traditional, TTP-centric security tools and the increasing sophistication of modern adversaries. It also reinforces the necessity of a defense-in-depth approach that combines preventive measures, like IAM and PAM, with deception-driven detection and swift response actions. By integrating complementary layers, organizations can enhance their resilience against evolving threats and protect their most critical assets.
To learn more about how Acalvio’s advanced deception technology can help your organization detect and stop threats that bypass traditional defenses, reach out to us today.




