Microsoft Active Directory Security Part 1: Understanding the Attack Surface
An Active Directory (AD) compromise has been at the core of several cyberattacks, such as the SolarWinds hack and the Ransomware attack on Colonial Pipeline. Potential vulnerabilities, such as nOAuth on Microsoft Azure Active Directory, have been identified by security researchers.
When the first version of Microsoft Active Directory was released two decades ago, it was built on the philosophy of inherent trust models within the boundaries of a network. Given these legacy architectural principles, Active Directory security is a challenge.
As an enterprise grows, new users, computers, applications, and cloud services are added to the enterprise network. Each addition is a new object that is managed in the AD. Administrators must set up new accounts, grant required permissions to these accounts, and enable these accounts to communicate with devices and applications. These factors make Microsoft Active Directory security very complex.
In this 3-part series, we look at protecting Microsoft Active Directory, which is central to most enterprise architecture. This series covers:
- Understanding the AD Attack Surface.
- A look at Attack Paths
- How Advanced Deception can be used to protect the AD.
This first blog discusses the AD Attack Surface and Microsoft Active Directory vulnerabilities that attackers can exploit to perform lateral movement, escalate privileges, and to maintain persistence in the enterprise network.
What is the Active Directory Attack Surface?
The Active Directory attack surface comprises all infrastructure elements, vulnerability vectors, and other factors in the AD ecosystem that attackers can use to enter, traverse through, or exit from the enterprise network.
As an example, the figure illustrates a few Active Directory elements and their misconfigurations that could create a high-risk attack surface for Active Directory attacks.
- Read-Only Domain Controllers (RODCs) can be used by adversaries to execute credential access attacks on privileged hosts or members of protected groups.
- Misconfigurations in non-human or service accounts can be leveraged to obtain Kerberos service tickets that adversaries can use to gather service passwords by offline cracking methods.
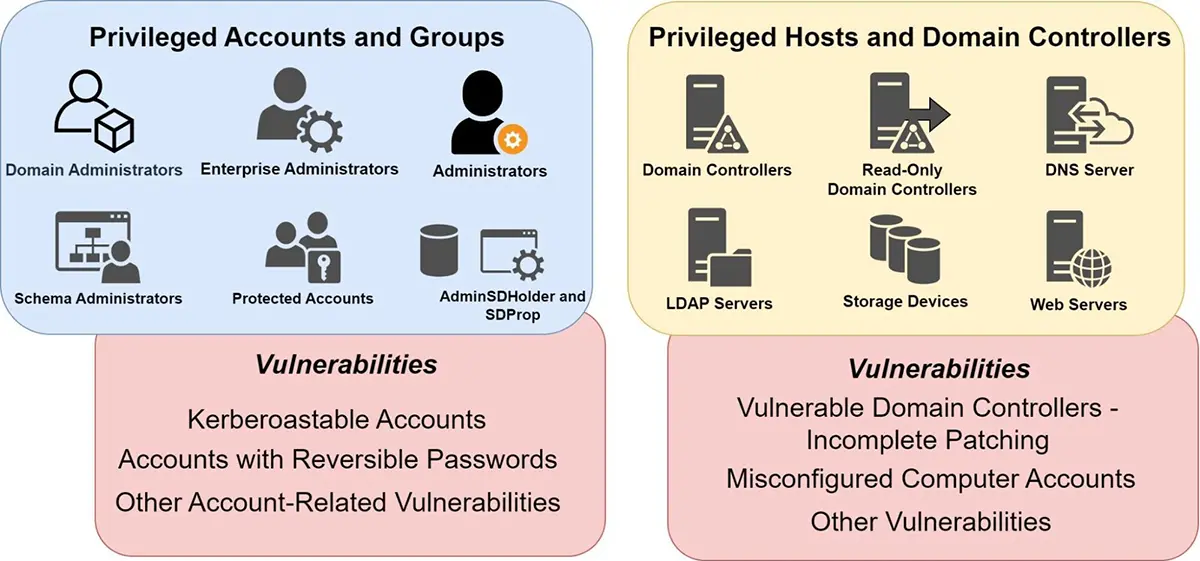
Technological advances in workforce mobility, digital transformation, and cloud adoption have led to a rapid increase in the attack surface area and potential for Active Directory attacks. In addition, everyday business events, such as new remote or branch office networks, onboarding of partners and contractors, and M&A integration activities, all contribute to a dynamically changing AD attack surface.
What are some AD Attack Surface Vulnerabilities?
The Active Directory attack surface is a broad and complex topic. Some specific Microsoft Active Directory vulnerabilities are summarized in this section.
Windows System and Active Directory Vulnerabilities
Over the lengthy lifespan of Windows Server and Active Directory, numerous vulnerabilities have been identified with low to critical scores on the CVSS scale. The ZeroLogon AD vulnerability (CVE-2020-1472) scored a 10/10 on the CVSS scale. This vulnerability allows an attacker to compromise the entire domain without even requiring a valid domain credential.
Microsoft regularly releases security patches. Security analysts closely track these vulnerabilities for disclosures, testing, and fix validations. However, deploying a patch and ensuring that the AD infrastructure is always on the latest release is a non-trivial task for any enterprise and leaves the network vulnerable to Active Directory attacks in the interim.
AD Misconfigurations
One of the most powerful Active Directory capabilities is flexible policy constructs. Unfortunately, this also is one of its biggest security drawbacks. User provisioning, computer/server management, groups management, ACLs, ACEs, GPOs, attribute populating for multiple object types are managed using various scripts and native methods for administration, such as PowerShell.
Although administration scripts provide a lot of flexibility, they create a high level of management complexity in the environment. As complexity grows, it causes numerous unknown dependencies and security misconfigurations.
Such misconfigurations can create security holes and widen the attack surface. The issue is compounded by the fact that these misconfigurations are hard to find and fix. They can also lead to undesired exposure.
Availability of Advanced Tools
Over the last few years, the cybersecurity community has made many technological advances in developing open-source Red Team tools. While these tools have been very beneficial for security teams, attackers have also adopted these tools which they can use to attack the Active Directory.
BloodHound, PowerSploit, MetaSploit, Mimikatz, Hashcat, Rubeus, ADRecon, Kekeo, DeathStar, PowerView, and many others are relatively easy to obtain. A tool like BloodHound can be used to very quickly discover relationships between various entities in the domain and calculate the shortest path between entities.
In addition to these open-source tools, attackers often use Living-off-the-Land (LotL) techniques by employing tools like Windows PowerShell, which are already available on endpoints and servers in the enterprise network. This approach helps attackers evade detection and stay hidden in the network for a long time.
What are some common AD Attack Surface Vulnerability Exploits?
The following examples show how attackers can leverage and exploit specific AD elements and vulnerabilities to carry out Active Directory attacks.:
Upgrade Deferral
An enterprise often runs critical applications, non-Windows servers, and systems that have been configured through older AD versions. Since an upgrade will be a huge task, Administrators may choose to defer even a recommended AD upgrade. This gives attackers a chance to exploit known vulnerabilities in the AD.
Over-Privileged Accounts
As user roles change, user accounts are given privileges by adding their accounts to groups such as the Domain Administrators and Enterprise Administrators groups.These privileges are not always withdrawn when they are no longer applicable. Attackers look at such accounts as prime targets for compromise.
Additional Domain Controller Apps
A Domain Controller (DC) sometimes runs additional applications and utilities unrelated to Active Directory. These applications and utilities significantly add to the AD attack surface by requiring configuration settings that open ports, access users who should not be connected to the DC, and create high-privileged service accounts.
Users often use a high-privilege account to log in to a DC and then use the same account, for example, to access the Internet and download freeware utilities. If such an account is compromised, attackers gain direct access to the DC.
Configuration Changes
Constant changes in AD object configurations may also lead to a transient attack surface and make Active Directory protection more difficult. In such situations, a dormant, persistent threat can exploit these for attack progression.
Patch Management Gaps
An enterprise may have gaps in its patch management systems and processes. Non-Windows operating systems, commercial applications, and networking devices may get patched only sporadically.
Patching that is incomplete or terminates with errors may not be reviewed and rectified. Since all assets are managed in the AD, any poorly patched asset that is compromised gives attackers a path to Active Directory attacks.
Outdated Antivirus Protection
Antivirus and antimalware software in server subnets may be misconfigured or outdated. Attackers can exploit these weaknesses to compromise a server, gain a foothold in the network, and reach the AD.
Legacy Protocol Risks
An enterprise may configure the AD to store LAN Manager hashes or reversibly encrypted passwords to support legacy authentication protocols. Attackers can employ standard methods to crack these passwords and gain access, weakening Active Directory protection.
Next Steps
Identifying all the elements and factors that make up the AD attack surface is the first step toward Active Directory protection. But this is a challenging task for security teams because the attack surface is constantly changing and expanding.
Given the central function of the AD, managing and minimizing its attack surface is not just a security responsibility, it requires cross-functional collaboration and commitment to AD attack surface monitoring and minimization.
In the next blog, we will cover how attackers can use various attack paths within the AD attack surface to achieve their objectives.
Frequently Asked Questions
The Active Directory attack surface comprises all infrastructure elements, vulnerability vectors, and other factors in the AD ecosystem that attackers can use to enter, traverse through, or exit from the enterprise network.
Understanding and mapping out the AD Attack Surface is the first step towards Active Directory security. Defense teams can use this information to mitigate vulnerabilities and preemptively reduce the attack surface.
In any enterprise, with continuous growth and restructuring, there is a complex and evolving ecosystem of users, computers, groups, GPOs, and other objects. This makes Microsoft Active Directory security very complex. Management blind spots, misconfigurations, inconsistent application of the latest patches, over-permissioned accounts, and inadequate access controls in the AD present significant security risks.
Attackers leverage several tools that were originally developed as Red Team tools for security teams. Tools such as BloodHound, PowerSploit, MetaSploit, Mimikatz, Hashcat, Rubeus, ADRecon, Kekeo, DeathStar, PowerView, and many others are relatively easy to obtain and can be leveraged to attack the AD.
The list of some common Active Directory attacks includes the following:
- Kerberoasting
- AS-REP Roasting
- Unconstrained Delegation Computer Attacks
- Recon Attacks
- DCSYNC
- Azure AD Connect Attacks
- ADFS/Golden SAML Attacks

