In the rapidly evolving world of cybersecurity, traditional Identity Threat Detection and Response (ITDR) systems are foundational in safeguarding organizational assets. Yet, these systems frequently display critical gaps, especially when faced with sophisticated, identity-based threats and the exploitation of system vulnerabilities. These traditional systems rely heavily on signature-based detection, anomaly behavior analysis, and logs, which may not effectively distinguish between legitimate activities and sophisticated malicious tactics. As attackers continue to evolve their techniques, especially in exploiting third-party components and using stolen credentials, the limitations of traditional ITDR become apparent.
Why attacks succeed: despite the deployment of traditional monitoring approaches on Active Directory (AD) and cloud identity stores, identity-based attacks are continuing to escalate at an alarming rate.
Attackers have evolved with stealthy techniques that exploit gaps in traditional ITDR for credential misuse and privilege escalation, such as:
Cached credentials: are copies of user authentication data stored locally to speed up re-authentication processes, including passwords, session tokens, and Kerberos tickets. While they enhance system performance and user convenience, they also provide attackers with a potential goldmine. Cybercriminals leverage tools like Mimikatz, LaZagne, Seatbelt, and other credential dumping utilities to extract these credentials from various caches (like Windows Security Accounts Manager (SAM), Local Security Authority Subsystem Service (LSASS) cache, and browser caches), enabling them to persist within networks, move laterally across systems, and escalate privileges. The subtlety of these attacks often allows them to bypass traditional security measures, which struggle to differentiate between legitimate and malicious use of these credentials.
Third-party sync agents and identity stores beyond AD: organizations are increasingly adopting a hybrid identity architecture with cloud identity providers (IdP) for identity federation. To keep AD in sync with the cloud IdP, synchronization agents are deployed. Additionally, organizations have servers such as Active Directory Federation Services (ADFS) and Active Directory Certificate Services (ADCS) that have trusted access to AD. Attackers target the third-party sync agents to gain access to domain credentials, leveraging the lack of monitoring on these agents to obtain access to privileged credentials.
Stealthy attacks that evade traditional detection mechanisms: attackers have evolved, with stealthy attacks such as offline attacks, client-side attacks that evade traditional detection approaches based on monitoring AD network traffic and logs. Offline attacks such as Kerberoasting, client-side attacks such as Silver Ticket attacks are being used with increasing frequency by attackers. These attack techniques do not result in anomalous network traffic or event log traces, resulting in detection gaps through traditional ITDR approaches.
Adversary in the middle (AITM) attacks: attackers gain access to domain credentials through AITM techniques such as LLMNR poisoning and use these credentials for lateral movement. Traditional ITDR is unable to detect malicious use of the valid credentials.
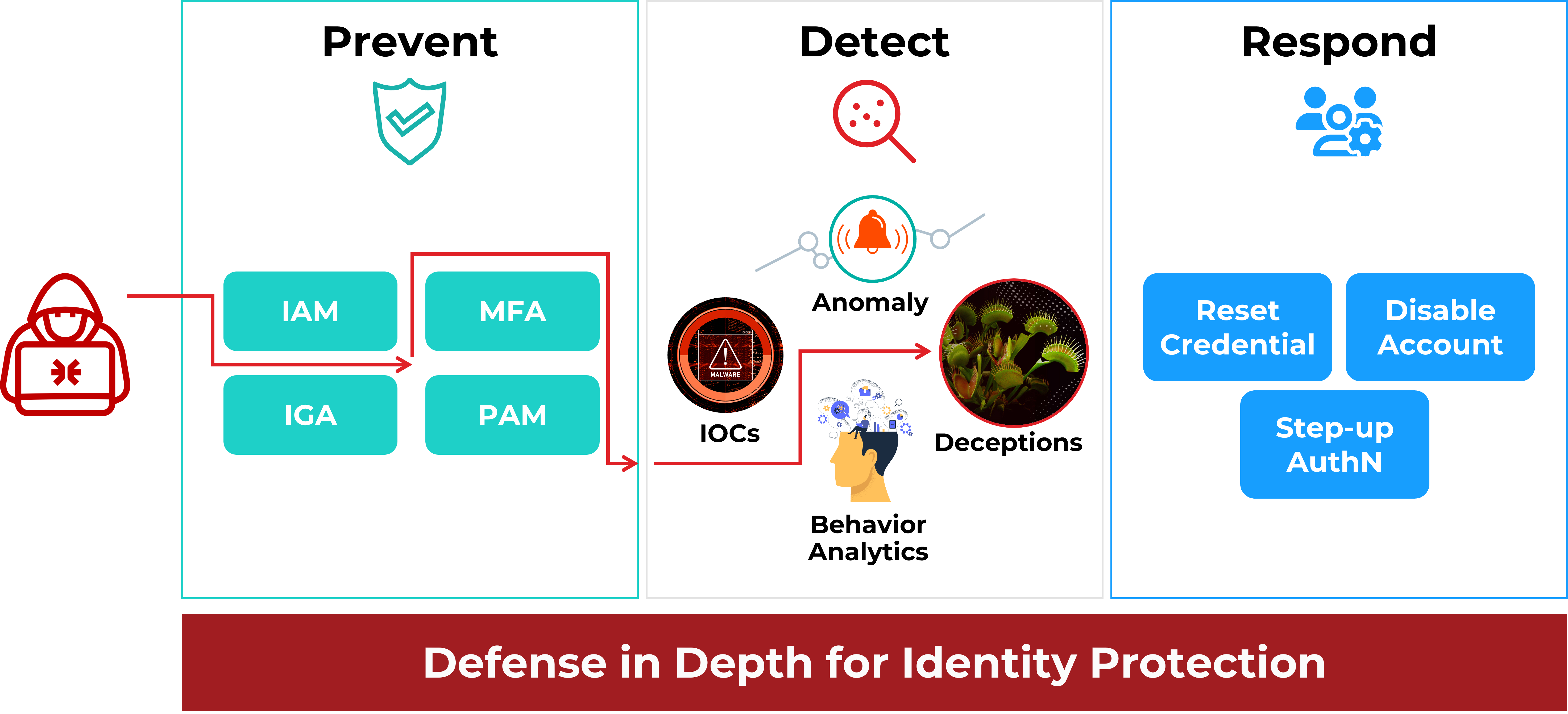
Cyber deception emerges as a critical solution to these challenges. It introduces deceptive elements, such as honey accounts and honeytokens, strategically placed within the identity stores and endpoints to lure and detect attackers by triggering undeniable indicators of an incursion. This proactive defense mechanism not only enhances detection capabilities but also provides actionable intelligence, enabling more effective and rapid response. By addressing the inherent weaknesses of conventional detection methods, especially in the context of cached credentials and stealthy identity attack techniques, cyber deception creates a more resilient and adaptive security posture against the increasingly complex threat landscape.
The Growing Need for Cyber Deception in ITDR
Modern ransomware and APT threats are continuing to escalate in frequency and impact despite traditional ITDR tooling being in place. Attackers are exploiting the gaps in traditional ITDR to breach the defenses. Identity-based attacks have continued to grow at an alarming pace in 2024, highlighting the need for strengthening cyber defense.
The anomaly-based detection systems result in associated false positives, making it challenging for SOC teams to investigate the alerts that have been raised. This results in an ever-widening detection gap, making it possible for lesser-skilled attackers to complete their objective owing to the alert backlog for SOC teams.
As attacks have increasingly adopted identity compromise, cybersecurity has needed to evolve beyond endpoint and network-centric defenses to an identity-centric defense approach. ITDR, with its focus on identity threats, is a robust framework and strategy to defend against modern cyber threats. To realize the value of ITDR, a defense-in-depth approach that combines detection approaches (anomaly and log-based detection combined with cyber deception) is essential.
How Cyber Deception Makes a Difference
- Early threat detection: Attackers gain initial access to an endpoint and attempt to exploit the identity architecture. Honeytokens deployed across the endpoints enable defense teams to detect the attack on the initial beachhead, enabling response actions to isolate the threat and protect the identity architecture.
- Comprehensive Identity Protection: Cyber deception eliminates the gaps associated with traditional ITDR, detecting attacks that exploit these gaps. Deception-based detection is agnostic to attacker TTPs, enabling continuing coverage as attackers evolve novel attack vectors.
- Precise Detection Engineering and Response: ITDR can provide actionable alerts by incorporating deception. Traditional detection might label many activities as “suspicious,” complicating the task of distinguishing between harmful and benign actions. Deception ensures that interactions with honeytokens are definitive indicators of malicious activity, thus streamlining the detection and response processes.
- Mislead and Slow Down the Attacker: The deployment of honeytoken accounts that are made vulnerable intentionally to attract attackers not only detects when an attack occurs but also misleads the attacker, wasting their resources and giving IT teams more time to respond.
Why It’s Essential
Identity-based attacks are resulting in large-scale breaches, despite the investment in traditional approaches to threat detection. With the rapid rise in adversarial AI, the threat landscape will continue to evolve and escalate, making it essential to adopt defense strategies that can detect evolving threats with precision. Cyber deception eliminates the gaps in traditional ITDR frameworks and brings precision and a proactive stance that is necessary to protect the identity architecture and stop breaches.
Acalvio is positioned as a leader in providing scalable, AI-driven deception solutions that integrate seamlessly with existing ITDR frameworks like CrowdStrike Identity Protection, Microsoft Defender for Identity, enhancing overall security posture and operational efficiency.
If you would like to learn more, please schedule an appointment [here]. More information on ITDR is also available [here].