- Products
-
ProductsPlatform
- ShadowPlex Advanced Threat Defense
Deception for early detection of cyber threats with precision and speed
- ShadowPlex Cloud Security
Multi-cloud Security Built on Enterprise-scale honeytokens
- ShadowPlex Identity Protection
Visibility of identity attack surface and comprehensive detection of identity threats
- ShadowPlex Threat Intel
Targeted Threat Intel Providing Preemptive Cyber Security
- Acalvio Active Defense Platform
Comprehensive and Award-winning Distributed Deception Platform
- What is Active Defense?
Active defense detects and diverts attacks.
- Why do I need Acalvio Active Defense?
Active Defense deceives and disrupts attackers.
- ShadowPlex Advanced Threat Defense
-
- Solutions
-
Technology SolutionsIndustry Solutions
- Early Threat Detection
Detect cyber threats early in the attack lifecycle to prevent adversary breakout
- Identity Threat Detection & Response
Detect identity threats with precision and protect the identity architecture
- OT Security
Protect OT environments from cyber threats with an easy-to-deploy and non-intrusive solution
- Red Teaming
Strengthen defenses to detect red team activities
- Threat Hunting
Active threat hunting to confirm latent threats and gain visibility to attacker TTPs
- Ransomware
AI-driven deception to protect against known and zero-day ransomware variants
- Honeytokens for CrowdStrike
Enterprise-scale honeytokens to protect against current and evolving identity threats
- Cloud Detection and Response (CDR)
Agent-less threat detection across multi-cloud environments using AI-Powered honeytokens
- Active Directory Protection
Visibility to AD attack surface and detection of AD attacks
- Zero Trust
Advance Zero Trust maturity through improved cyber visibility
- Insider Threats
Unmask hidden dangers. Cyber deception for high-fidelity insider threat detection
- Public Sector
Targeted solution for protecting Federal agencies in conformation with NIST and CISA recommendations
- Financial Services
Transform Financial Cybersecurity with Innovative Cyber Deception and Active Defense
- Healthcare
Active defense solutions thwart healthcare attacks before they can inflict real damage.
- Early Threat Detection
-
- Resources
- Partners
- Company
Botnet
What Is a Botnet?
A botnet, short for “robot network,” is an intricate web of interconnected devices, referred to as “bots” or “zombies.” The Botnet definition can include computers and IoT/IIoT devices. These are devices that have been hijacked and infected with malicious software, transforming them into obedient foot soldiers at the command of a central authority.
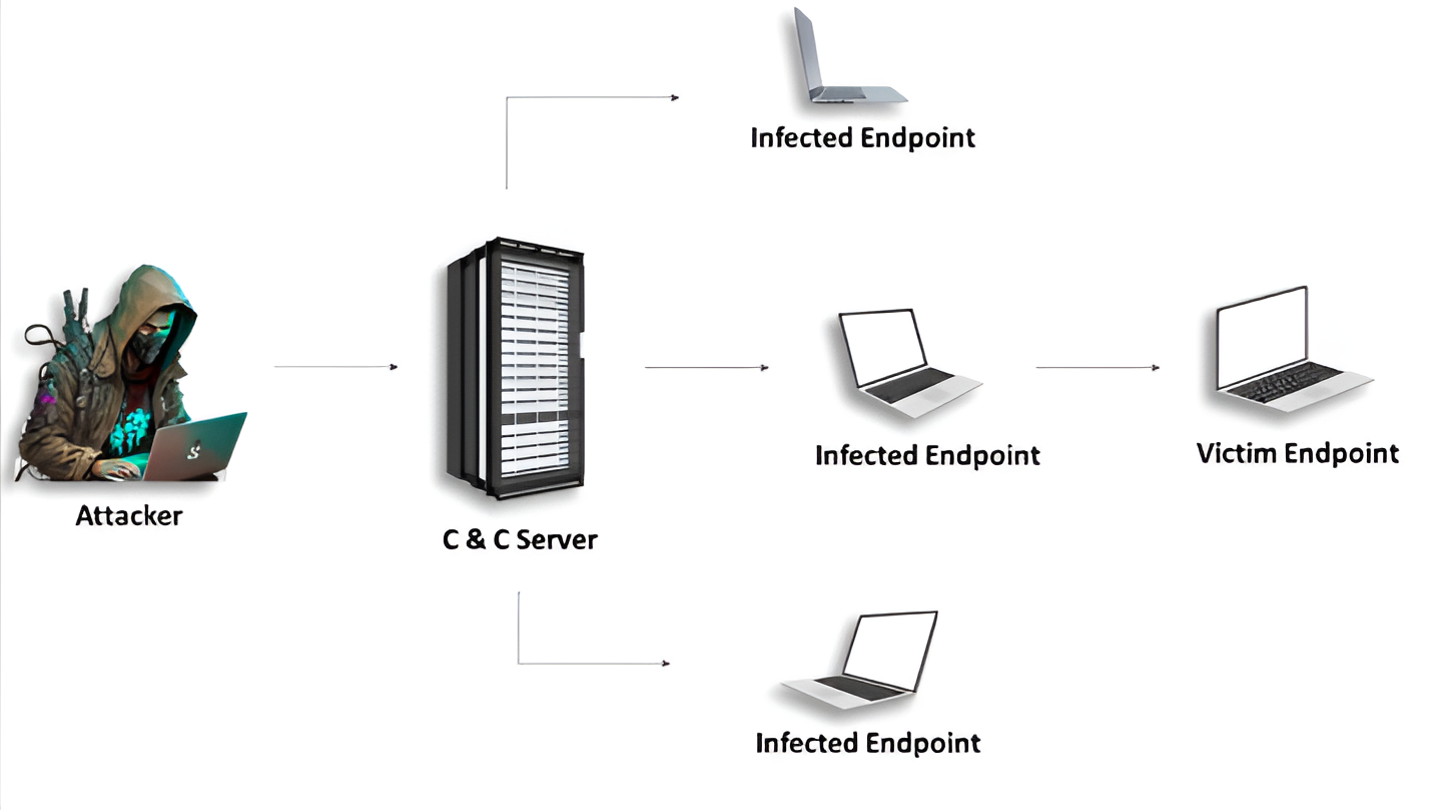
Why Are Botnets Created?
Botnets are created for malicious purposes, typically by hackers seeking to exploit large networks of compromised devices.
Botnets are commonly used to launch Distributed Denial of Service attacks, where large numbers of compromised devices are instructed to flood a target (such as a website or online service) with traffic, overwhelming it and causing it to crash or become unavailable. Botnets are often used to send massive amounts of unsolicited emails, advertisements, or phishing messages. The large network of compromised devices allows attackers to send out millions of spam emails while hiding their real identity.
Botnets can be used to steal sensitive information such as passwords, banking credentials, or personal data from infected devices. The malware running on these devices can record keystrokes (keylogging), capture screenshots, or even directly search for files containing valuable data. Botnets can be used to generate fake clicks on advertisements, inflating the ad revenue of websites controlled by the attacker. Some groups create botnets to sell or rent them to other criminals.
What Are the Methods of Botnet Propagation?
Botnets propagate through various methods, using some of the primary methods described below:
Exploitation of Vulnerabilities:
Cybercriminals exploit known software vulnerabilities in target devices, gaining unauthorized access to implant bot software and subjugating them to the botnet.
Social Engineering and Phishing:
Deceptive tactics, such as phishing emails with malicious attachments or links, can coerce users into unwittingly installing bot software on their devices.
Drive-by Downloads:
Malicious code concealed on compromised websites takes advantage of visitors’ vulnerable systems, covertly downloading bot software without their knowledge.
Trojan Horse Techniques:
Some botnets are distributed through Trojan horse programs that disguise themselves as legitimate software, only to unleash bot software upon installation.
How Do Botnets Work?
Botnets are formidable tools for unleashing cyber attacks with widespread impact. These networks of compromised devices, under the control of a single entity, can execute a variety of malicious activities.
Botnets launch Distributed Denial of Service (DDoS) attacks by overwhelming targets with a barrage of traffic, rendering services inaccessible. They spread malware by sending malicious emails or exploiting vulnerabilities, initiating data breaches and ransomware infections.
Botnets also engage in credential stuffing, using stolen passwords to compromise accounts. Additionally, they exploit compromised devices to mine cryptocurrencies, creating financial gain for attackers.
Their agility and ability to coordinate attacks make botnets a persistent and evolving threat to digital infrastructure and data security.
Types of Botnet Attacks
Distributed Denial-of-Service (DDoS) attacks
This is the most common type of botnet attack. In a DDoS attack, the botnet sends a flood of malicious traffic to a target website or server, causing it to become overwhelmed and unavailable.
Malware distribution
Botnets can be used to distribute malware, such as viruses and trojans. This malware can then be used to steal data, install other malware, or take control of the victim’s device.
Phishing attacks
Botnets can be used to send phishing emails or text messages. Botnet phishing emails or text messages often appear to be from a legitimate source, such as a bank or credit card company. When the victim clicks on a link in the email or text message, they are taken to a fake website that looks like the real website. After the victim enters their personal information on the fake website, the attacker can steal it.
Click fraud
Botnets can be used to click on ads on websites. This can generate revenue for the attacker, as the advertiser is charged each time their ad is clicked on.
Censorship circumvention
Botnets can be used to circumvent censorship by bypassing blocks on websites or social media platforms. This can be used to spread propaganda or to access information that is not available in the victim’s country.
Stealth mining
Botnets can be used to mine cryptocurrency without the victim’s knowledge. This can drain the victim’s battery and use up their bandwidth.
Sniffing and keylogging botnet attacks
Sniffing and keylogging botnet attacks are malicious techniques used by cybercriminals to capture sensitive information from infected devices. In sniffing attacks, botnets monitor and intercept network traffic, often targeting unencrypted communication to steal login credentials, personal data, or financial information. Keylogging botnets, on the other hand, install software on compromised devices that secretly records every keystroke made by the user, allowing attackers to gather passwords, credit card numbers, and other sensitive information. These attacks are often difficult to detect because the botnet operates quietly in the background, making it easier for attackers to gather data without the victim’s knowledge, leading to potential identity theft, financial loss, and privacy violations.
Large-scale spam attacks
Large-scale spam attacks involve the use of botnets to send massive volumes of unsolicited emails, often with the intent to spread malware, promote phishing schemes, or advertise fraudulent products and services. These attacks typically rely on networks of infected devices, or “zombies,” that distribute spam messages to a wide range of recipients. The emails may contain malicious attachments, links to fake websites, or misleading offers to deceive recipients into disclosing personal information. Due to the sheer volume of spam, these attacks can overwhelm email systems, clog inboxes, and make it difficult for legitimate communications to be received. Large-scale spam attacks can also be used as a tool for launching other cybercrimes, including data theft or spreading ransomware.
Data breach perpetrated via botnets
A data breach perpetrated via botnets occurs when a network of compromised devices is used to infiltrate and exploit vulnerable systems, leading to unauthorized access and the theft of sensitive information. Botnets, made up of infected devices such as computers, IoT devices, and servers, can be directed by cybercriminals to carry out coordinated attacks on target networks. Once inside, the botnet can silently exfiltrate valuable data like personal details, financial records, intellectual property, or login credentials. These breaches can go undetected for extended periods, allowing attackers to harvest large quantities of data, which can then be used for identity theft, financial fraud, or sold on the dark web. The use of botnets in data breaches significantly increases the scale and complexity of such attacks, making them difficult to prevent and mitigate.
Brute force attacks
Brute force attacks are a type of cyberattack where an attacker uses automated software or botnets to systematically try every possible combination of passwords or encryption keys until the correct one is found. These attacks rely on the sheer processing power of compromised devices to generate and test a large number of potential passwords at high speeds. While brute force attacks can target any type of authentication system, they are particularly effective against weak or simple passwords. The attack continues until access is granted, potentially allowing the attacker to gain unauthorized control over user accounts, networks, or systems. To defend against brute force attacks, it’s crucial to implement strong, complex passwords, multi-factor authentication, and account lockout mechanisms that limit the number of incorrect login attempts.
Credential Theft
Credential theft is a cybercrime where attackers steal login credentials, such as usernames and passwords, to gain unauthorized access to user accounts, systems, or networks. This type of attack is commonly carried out through methods like phishing, where victims are tricked into providing their credentials via fraudulent emails or websites, or through malware, such as keyloggers, that secretly record keystrokes. Botnets can also play a role in credential theft by infecting large numbers of devices and capturing login details without the user’s knowledge. Once stolen, the credentials can be used to access sensitive information, perform financial fraud, or further infiltrate systems for malicious purposes. Credential theft poses a significant risk to personal, corporate, and governmental data security, often leading to identity theft, data breaches, or even ransomware attacks.
Cryptocurrency Mining
Cryptocurrency mining via botnets involves the illicit use of infected devices to mine digital currencies, such as Bitcoin or Ethereum, without the knowledge or consent of the device owners. Botnets, composed of compromised computers, IoT devices, or servers, are controlled by cybercriminals who redirect the processing power of these devices toward mining operations. As mining requires significant computational resources, this can cause system slowdowns, overheating, and a drastic increase in energy consumption for the affected users. The stolen computational power is then used to mine cryptocurrency, which is often converted into profits for the attackers. Cryptocurrency mining botnets are particularly dangerous because they exploit vulnerabilities in devices, leaving users unaware of the exploitation while their resources are drained for malicious gain.
The Growing Threat of Botnets
Predicted botnet threats pose a significant concern in the evolving cybersecurity landscape. As these malicious networks grow more sophisticated, they’re expected to leverage artificial intelligence and machine learning to enhance attack strategies, making them even harder to detect and combat.
The infiltration of Internet of Things (IoT) devices is likely to rise, exploiting their weak security. Botnets may collaborate with other malware for more devastating combined attacks. Political and geopolitical motivations could drive botnets to influence public opinion or disrupt critical infrastructure.
Supply chain attacks might exploit vulnerabilities within software vendors or service providers. Despite ongoing efforts to counter botnets, their adaptability and innovation continue to pose substantial risks to digital ecosystems.
Traditional security solutions often struggle to effectively detect and prevent botnet attacks due to the dynamic and evolving nature of these threats. Botnets employ sophisticated tactics, leveraging encryption, obfuscation, and decentralized command structures to evade signature-based detection methods.
Their distributed nature makes them harder to pinpoint, as individual compromised devices may exhibit seemingly benign behavior. Moreover, the sheer scale of botnets enables them to overwhelm traditional security defenses, such as firewalls and antivirus software.
Additionally, the increasing use of zero-day exploits and polymorphic malware allows botnets to exploit vulnerabilities before security patches can be applied. These factors collectively undermine the efficacy of conventional security measures, necessitating the adoption of advanced and adaptive strategies to effectively combat botnet attacks.
Preventing Botnet Attacks
Preventing botnet attacks is crucial for maintaining the security of a company’s network and systems. What is a botnet attack? A botnet attack occurs when a group of compromised computers, called “bots” or “zombies,” are remotely controlled by attackers to execute malicious activities.
To defend against these attacks, companies should adopt a multi-layered approach:
- Use firewalls to monitor and filter incoming and outgoing network traffic, intrusion detection systems that can detect abnormal network traffic patterns, and endpoint protection that can detect botnet infections.
- Ensure all software, including operating systems, applications, and firmware, is up to date. Many botnets exploit vulnerabilities in outdated systems.
- Implement MFA for all sensitive access points to reduce the risk of botnet actors gaining unauthorized access.
- Segment networks to limit the spread of botnet infections and contain damage if an attack occurs.
- Adopt a “zero trust” model, ensuring that no entity is trusted by default, even those within the corporate perimeter.
- Enforce strong password policies, such as complex passwords and regular updates.
- Maintain regular backups of critical systems and data to minimize disruption in the event of a successful attack.
Can Acalvio Be Used to Enable Botnet Protection in the Enterprise?
Acalvio’s Advanced Deception Technology offers a powerful approach to mitigating botnet threats by diverting and misleading attackers, thereby minimizing their ability to infiltrate and propagate within a network. By deploying deceptive elements like decoys, files, and credentials, organizations can create a virtual minefield that misleads and distracts botnets.
When bots interact with these decoys, security teams receive early alerts, enabling rapid response and containment. Furthermore, deception technology enhances threat detection by capturing attacker tactics, techniques, and procedures, facilitating in-depth analysis and proactive countermeasures.
It effectively disrupts botnet communication channels, exposes their presence, and hinders their lateral movement, substantially impeding their ability to carry out malicious activities and reducing the potential impact of botnet-driven attacks.
For more information about how Acalvio can be used to protect against cybersecurity threats like botnets, check our Advanced Threat Defense product.
Frequently Asked Questions
What is a botnet, and how do cybercriminals create and control them?
Why do hackers use botnets?
What is an example of a botnet attack?
What are the signs that a device may be part of a botnet?
How can organizations detect and mitigate botnet activity?
To detect and mitigate botnet activity, organizations can:
- Continuously monitor network traffic for unusual spikes or anomalies that could indicate botnet activity, such as large numbers of requests to a specific server.
- Leverage behavioral analytics and machine learning to detect patterns of traffic that deviate from the norm, which might suggest botnet-controlled devices.
- Use firewalls to monitor and filter incoming and outgoing network traffic.
- Ensure all software, including operating systems, applications, and firmware, is up to date. Many botnets exploit vulnerabilities in outdated systems.
- Segment networks to limit the spread of botnet infections and contain damage if an attack occurs.
- Maintain regular backups of critical systems and data to minimize disruption in the event of a successful attack.