- Products
-
ProductsPlatform
- ShadowPlex Advanced Threat Defense
Deception for early detection of cyber threats with precision and speed
- ShadowPlex Cloud Security
Multi-cloud Security Built on Enterprise-scale honeytokens
- ShadowPlex Identity Protection
Visibility of identity attack surface and comprehensive detection of identity threats
- ShadowPlex Threat Intel
Targeted Threat Intel Providing Preemptive Cyber Security
- Acalvio Active Defense Platform
Comprehensive and Award-winning Distributed Deception Platform
- What is Active Defense?
Active defense detects and diverts attacks.
- Why do I need Acalvio Active Defense?
Active Defense deceives and disrupts attackers.
- ShadowPlex Advanced Threat Defense
-
- Solutions
-
Technology SolutionsIndustry Solutions
- Early Threat Detection
Detect cyber threats early in the attack lifecycle to prevent adversary breakout
- Identity Threat Detection & Response
Detect identity threats with precision and protect the identity architecture
- OT Security
Protect OT environments from cyber threats with an easy-to-deploy and non-intrusive solution
- Red Teaming
Strengthen defenses to detect red team activities
- Threat Hunting
Active threat hunting to confirm latent threats and gain visibility to attacker TTPs
- Ransomware
AI-driven deception to protect against known and zero-day ransomware variants
- Honeytokens for CrowdStrike
Enterprise-scale honeytokens to protect against current and evolving identity threats
- Cloud Detection and Response (CDR)
Agent-less threat detection across multi-cloud environments using AI-Powered honeytokens
- Active Directory Protection
Visibility to AD attack surface and detection of AD attacks
- Zero Trust
Advance Zero Trust maturity through improved cyber visibility
- Insider Threats
Unmask hidden dangers. Cyber deception for high-fidelity insider threat detection
- Public Sector
Targeted solution for protecting Federal agencies in conformation with NIST and CISA recommendations
- Financial Services
Transform Financial Cybersecurity with Innovative Cyber Deception and Active Defense
- Healthcare
Active defense solutions thwart healthcare attacks before they can inflict real damage.
- Early Threat Detection
-
- Resources
- Partners
- Company
ITDR
What is Identity Threat Detection and Response (ITDR)?
Identity Threat Detection and Response (ITDR) focuses on protecting identity management infrastructure from various attacks. ITDR tools and practices aim to block and detect threats, verify administrator credentials, respond to identity-related attacks, and restore normal operations. Common threats that ITDR addresses include phishing, stolen credentials, insider threats, and ransomware.
ITDR adds an extra layer of security to traditional identity and access management (IAM) systems by enhancing their capabilities with continuous monitoring and response functionalities. This involves leveraging identity analytics, machine learning, behavioral analysis techniques, and anomaly detection to identify and mitigate potential threats in real-time. ITDR solutions also integrate with existing security frameworks, like endpoint detection and response (EDR), to provide comprehensive protection.
Enhance Security with Deception-Based ITDR
Traditional security perimeters are changing with the advent of remote work and the proliferation of SaaS services. Attackers increasingly exploit identities to infiltrate enterprise resources. With an alarming 80% of breaches involving compromised identities, the urgency for a robust defense mechanism has never been more critical.
Despite having Identity Governance and Administration (IGA), Identity and Access Management (IAM) solutions in place, organizations remain vulnerable to identity-based attacks.
IGA and IAM focus on policy enforcement and access control. They lack dynamic threat detection capabilities. Attackers continuously develop new techniques. They exploit gaps that policy-based solutions can’t anticipate or adapt to. Traditional tools miss real-time threats.
Defense-in-depth is needed for multi-layers of protection. Identity threat detection and response (ITDR) fills a critical need for identity-centric detection. Deception technology is a proven approach for detecting current and evolving identity threats with precision and speed.
How ITDR Works
An effective strategy for identity protection involves a layered approach that combines prevention (Identity ASM) and threat detection (ITDR) strategies.
Traditional security solutions cannot differentiate between legitimate and malicious usage of trusted identities. Attackers exploit this limitation by employing stealthy exploits such as client-side attacks, offline attacks, and zero-days to evade traditional security measures. Deception-based Identity Threat Detection and Response (ITDR) is a powerful solution that provides early and precise detection for a diverse range of identity threats.
What is the difference between ITDR, EDR, and XDR?
ITDR protects identities and identity management infrastructure. It focuses on detecting, responding to, and mitigating threats related to user credentials, privileges, and identity systems. EDR is designed to protect endpoint devices such as laptops, desktops, and servers. It focuses on detecting and responding to threats that target these devices. XDR aims to provide a more integrated and comprehensive approach by extending the capabilities of EDR across multiple security layers including network, endpoint, server, and email security.
ITDR covers identity systems, credentials, and user activities. EDR covers endpoints and devices. XDR spans the entire security ecosystem, integrating multiple data sources.
Why do organizations need ITDR?
Organizations need Identity Threat Detection and Response (ITDR) for several critical reasons:
- Rising Identity-Based Attacks: There is a significant increase in the risk posed by stolen or compromised credentials.
- Complex Identity Environments: As organizations adopt multi-cloud architectures, managing identities across different environments becomes more complex. ITDR provides visibility and control over these distributed identity systems.
- Proactive Threat Detection: ITDR solutions continuously monitor for unusual identity-related activities, enabling early detection and response to potential threats before they can escalate.
- Zero Trust Framework: ITDR supports the Zero Trust security model by continuously validating and monitoring identities, ensuring that only authorized and authenticated users have access to critical resources.
- Regulatory Compliance: Many regulatory frameworks and standards require robust identity management and protection measures.
How Acalvio Can Help with ITDR
Acalvio ShadowPlex Identity Protection is designed to safeguard identities and enhance the implementation of Zero Trust principles, enabling a proactive and resilient security posture.
The solution combines identity attack surface management capabilities for proactive security with deception-based identity threat detection and response (ITDR) capabilities for comprehensive threat detection.
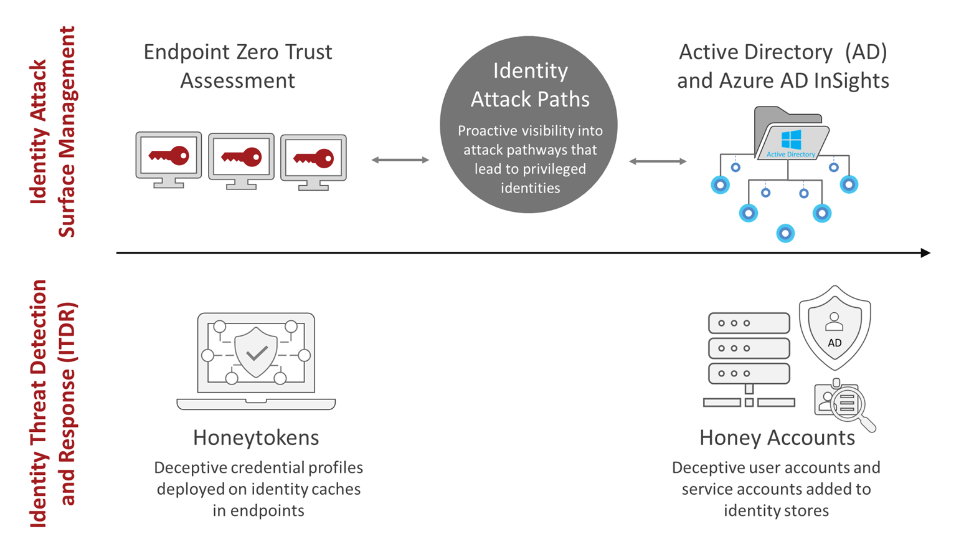
ShadowPlex Identity Protection combines Identity Attack Surface Management and Deception-Based Identity Threat Detection and Response (ITDR)
ShadowPlex ITDR includes:
Identity Attack Surface Management (ASM): provides proactive visibility into the identity attack surface within identity stores and on endpoints, offering a unique “attacker view” for defense teams.
Identity Attack Paths: Identifies the pathways attackers use to gain access to privileged identities or critical assets. This functionality also empowers defense teams by revealing the potential “blast radius” of an attacker originating from a compromised identity or endpoint.
Honey Accounts and Honeytokens: Honey Accounts are deceptive user and service accounts embedded within identity stores, while Honeytokens are misleading credential profiles found on endpoints. These elements work in tandem to facilitate deception-based ITDR, providing a robust mechanism for detecting a wide array of identity threats.
Acalvio ShadowPlex ITDR is equipped to detect stealthy and evolving identity threats that evade traditional security. It detects APT threat actors and modern ransomware that leverage identities to launch attacks on the enterprise network.