Resources
Don’t be a sitting duck. Make your BreadCrumbs & Lures Dynamic!
BreadCrumbs and Lures are very critical components of any deception based architecture. As the name suggests, breadcrumbs and lures aid to divert a threat a threat actor (an individual or malware) to deception sensors. The moment the deception sensor gets tripped,...
Reflections on a conference…
This past week I’ve spent 30 hours in planes and countless more hanging around in security lines, I’ve been heated to the point of melting, tired to the point of sleeping while standing and stressed to the point of immobility (mostly my fault due to not getting all...
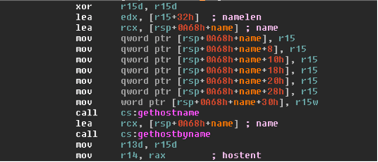
Technical Analysis of Petya
Acalvio Threat Research Labs Petya is the most recent ransomware strain. It originated in Ukraine [1] and is spreading across Europe. This blog summarizes our technical analysis of Petya. Technical Analysis In addition to the encryption and ransomware functionality,...
Ransomware: Catch me if you can.
Ransomware demand in 2016 was around a billion dollars[1]. WannaCry[3] was the recent ransomware campaign that spread across 150 countries affecting 200,000 users. It is estimated that in 2017[2], damages due to ransomware will exceed $5 billion. Modern defenses make...
The Industry’s First “Deception 2.0 for Dummies” Book
Since the dawn of time, deception has been used in nature in various forms as a successful survival strategy and has played an important role in the physical and behavioral adaptations of all organisms. Humankind, with its higher cognitive ability, has successfully...
How to outfox Shamoon? Put Deception to work!
Acalvio Threat Labs Shamoon is one of the critical threats that has been able to penetrate traditional defenses successfully not once, twice, but thrice - in 2012, 2016 and 2017. The main purpose of Shamoon Threat Actor was the destruction of the endpoint computers...
Honeypots are dead! Long live Honeypots (Part4…The Crystal Ball)
Self healing system capabilities, specifically analysis and intelligence shared between Acalvio instances so you end up with a worst case scenario of only company1 getting hit, companies 2,3,4 have automatically learned from company1. IoT, V2V, V2X etc. This...
2017 Predictions AND “wants”
Going to do this one a little differently, part of it is going to be the typical “throw the crystal ball over the shoulder” stuff that we all do…although honestly JUST going to 2017 is not far enough for some of the stuff we are working on…and the other part of this...
Honeypots’ Evolution: The Future Changes (Part 3) – Acalvio
In days gone past (and arguable in the current timeline we occupy) I would simply launch from the existing machine like an Olympic diver off the high board and go about my merry way for an “industrial average” of 200 days or thereabouts before ANYONE even knows or...
Looking Deeper into a Multi Stage Attack
The majority of today’s breaches are comprised of sophisticated multi-stage attacks. The stages of such attacks can best be described by a “Cyber Kill Chain”, which breaks down cyber intrusions into the following steps: Recon → Weaponize → Deliver → Exploit →...
Honeypots are dead! Long live Honeypots (Part2…Landed, Now What?)
Quick Recap: Initial Reconnaissance - Complete Initial Compromise - Complete Establish Footholds - Now Escalate Privileges Additional Reconnaissance where we will move laterally and continue to maintain presence Complete We now need to maintain presence on the...
Honeypots Reimagined: Many Targets, One Access (Part 1) – Acalvio
Initial Reconnaissance – About to explain Initial Compromise – About to launch Establish Footholds - Escalate Privileges Additional Reconnaissance where we will move laterally and continue to maintain presence Complete Initial Reconnaissance: “Let me show you how I...