- Detect threats during reconnaissance, credential harvesting, and lateral movement.
- Unify threat detection across IT networks, OT environments, and identity paths.
- Deploy authentic decoys supporting a wide range of OT protocols and asset types.
- Lure attackers away from production assets into decoy environments—safely and silently.
Adversaries are exploiting IT and OT assets in new, faster, and stealthier ways.
- Ransomware is one of the top threats targeting OT environments.
- Variants like Lockbit and Alphv now disrupt OT operations directly.
- ICS-specific malware like Pipedream targets OT protocols and devices.
- Attacks exploit vulnerabilities unique to industrial environments.
- Insiders with trusted access pose a major risk to IT and OT assets.
- Credential misuse often goes undetected without early deception.
- Adversaries leverage identity-driven attacks to compromise IT and OT systems.
- Active Directory and cloud identity paths are frequent targets in OT breaches.
- Malicious code is injected into OT software or hardware supply chains.
- Attackers exploit trusted vendors to bypass perimeter defenses.
- Attackers weaponize unknown vulnerabilities across OT protocols and devices.
- Early detection is critical before exploits impact operations.

Disrupt Ransomware Early
- Detects early lateral movement and credential misuse used in ransomware staging.
- Deception assets trigger high-fidelity alerts before encryption or disruption can occur.
- Protects critical OT production assets by diverting attackers to decoys.
- Operates agentlessly, ensuring no impact on fragile OT systems.

Catch ICS Malware Fast
- Deploys deception assets that mimic ICS devices and protocols (e.g., Modbus, DNP3).
- Detects malicious reconnaissance against industrial control systems early.
- Captures attacker behavior even when ICS-specific exploits are used.
- Provides high-fidelity telemetry without interfering with production ICS environments.

Expose Insider Moves
- Seeds deceptive credentials and access paths inside OT and IT environments.
- Detects insider lateral movement and credential misuse invisibly.
- Exposes privilege escalation attempts before critical systems are reached.
- Provides intent-based visibility without impacting operational workflows.

Secure Identity Paths
- Protects Active Directory extensions into OT with deceptive service accounts and credentials.
- Detects credential harvesting and misuse tied to identity paths.
- Surfaces attacker attempts to pivot from IT to OT environments early.
- Aligns detections with MITRE ATT&CK and MITRE ICS techniques.

Block Supply Chain Attacks
- Deploys deception inside vendor-accessible OT systems and services.
- Detects malicious software behavior before it impacts critical operations.
- Exposes attacker movement through third-party or remote access pathways.
- Provides early alerts without relying on known malware signatures.

Uncover Emerging Threats
- Identifies abnormal reconnaissance and access behavior without needing prior knowledge.
- Deception assets trigger alerts when unknown exploits are tested.
- Detects attacker intent even when using novel or sophisticated techniques.
- Provides critical early warning when traditional defenses may fail.

- Deploy Deception Across OT Networks
- Detect Unauthorized Reconnaissance and Access.
- Trigger High-Fidelity Alerts Based on Engagement
- Divert Attackers Safely Away From Production Assets
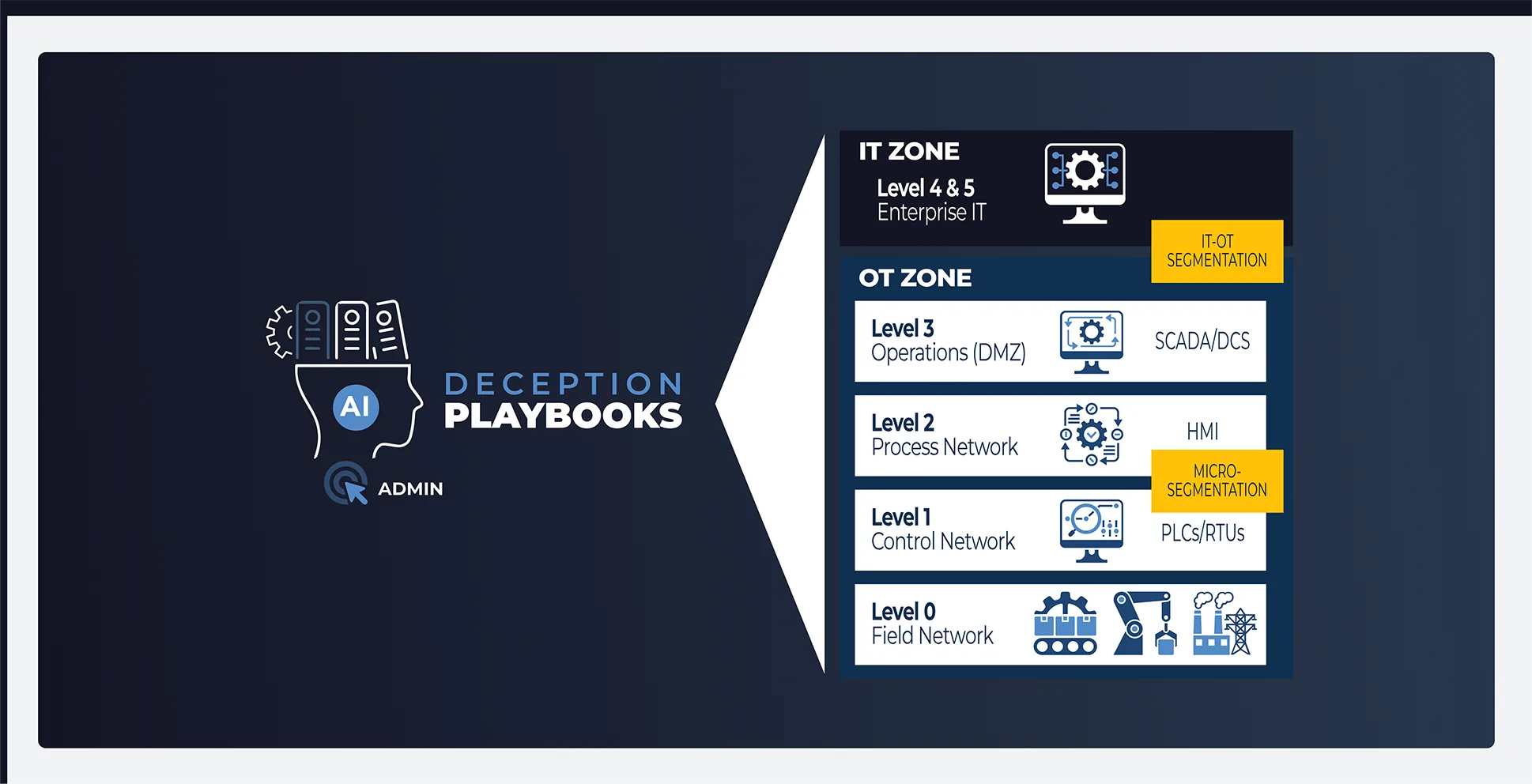
Represent assets across all levels of OT reference architecture.

Preemptive Cybersecurity for the OT Environment
The Honeywell Threat Defense Platform (HTDP) uses Acalvio’s AI-driven deception to protect vulnerable, connected OT systems with early, high-fidelity threat detection—without operational disruption.
- Safeguard OT environments where traditional security tools are too heavy or intrusive
- Detect attacker activity early without impacting OT systems or overwhelming teams with false positives.
Built for Operational Integrity. Focused on Preemptive Defense.
- Deploy agentless deception—no impact to OT systems.
- Safeguard devices without scanning or log access.
- Expose attackers during reconnaissance and lateral movement.
- Detect threats based on behavior, not network anomalies.
- Get verified alerts from real attacker engagement.
- Map detections to MITRE ICS for faster, focused response.
Frequently Asked Questions
Adversary breakout time is the duration an attacker takes to move from the initial compromise to broader network access. A shorter breakout time allows attackers to escalate their activities quickly, causing significant damage before detection. Effective defenses focus on minimizing breakout time through continuous monitoring, rapid detection, and network segmentation to limit lateral movement. Reducing breakout time enables faster response and helps mitigate the overall impact of an attack.
Traditional security solutions, like antivirus and firewalls, are often ineffective against new or unknown threats because they rely on known signatures and predefined rules. They struggle to detect modern, dynamic attacks, such as zero-day exploits or advanced persistent threats (APTs), which involve anomalous behavior. To address this, organizations require advanced detection methods like behavioral analysis, machine learning, and real-time threat intelligence for early threat identification and proactive response.
Cyber deception enables early threat detection by deploying decoy systems and data that appear legitimate to attackers. When attackers interact with these decoys, security teams are alerted, enabling early identification of threats. This approach helps organizations detect and respond to attacks before significant damage occurs, enhancing overall security.


