- Identify credential misuse, unauthorized access, and path discovery.
- Surface threats before encryption or breakout begins.
- Detect ransomware regardless of language, signature, or tooling.
- Catch RaaS-based and zero-day attacks in real time.
- Deploy deception on systems where EDR can’t reach.
- Cover jump servers, legacy endpoints, and unmanaged infrastructure.
- Trigger alerts only on real attacker interaction.
- Initiate isolation with SOAR and EDR integrations

- Detect credential misuse, identity abuse, and privilege escalation.
- Surface lateral movement and reconnaissance prior to encryption.
- Identify path discovery and domain enumeration activity.
- Reveal early-stage staging behaviors used to launch ransomware attacks.

- Detect ransomware built in Rust, Go, and other evasive languages.
- Catch threats that bypass AV and EDR with obfuscation or packing.
- Uncover behaviorally similar variants—even without IOCs.
- Recognize RaaS toolkits regardless of delivery or mutation.

- Cover unmanaged endpoints, jump servers, and cloud workloads.
- Deploy deception without relying on agents or scans.
- Automatically refresh deceptive assets to maintain realism at scale.
- Extend protection to legacy and air-gapped environments.
- Alert only when ransomware engages with deception.
- Eliminate false positives and reduce response fatigue.
- Feed intent-rich signals into SOAR, SIEM, and EDR workflows.
- Automate playbook-driven isolation before encryption begins.
Ransomware has evolved from automated malware into human-operated campaigns that behave like APTs. Attackers now use valid credentials, adapt to defenses in real time, and exfiltrate data before encryption even starts.
Why Traditional Tools Fall Short:
- Signature and anomaly-based tools can’t detect early identity abuse
- Agent-based tools miss jump servers, unmanaged systems, and memory-only execution
- Most defenses react after encryption has already begun
Why Thwarting Ransomware Requires Deception:
- Detects ransomware before encryption or exfiltration
- Triggers on early behaviors like credential misuse, lateral movement, and staging
- Provides intent-based alerts, not speculative anomalies
- Protects across EDR blind spots without relying on signatures or agents
Ransomware Has Outgrown Traditional Defenses
Modern ransomware doesn’t just drop a payload — it acts like an APT.
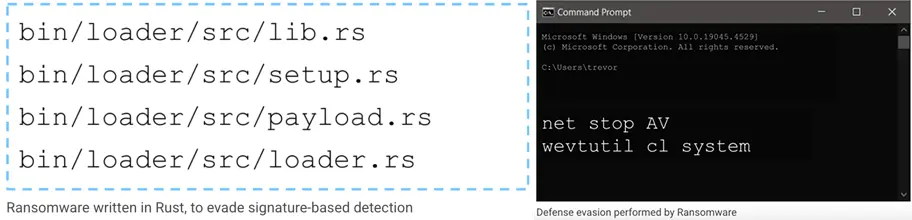
Attackers now use valid credentials, write in modern languages like Rust to avoid signatures, and operate in memory to evade agents.
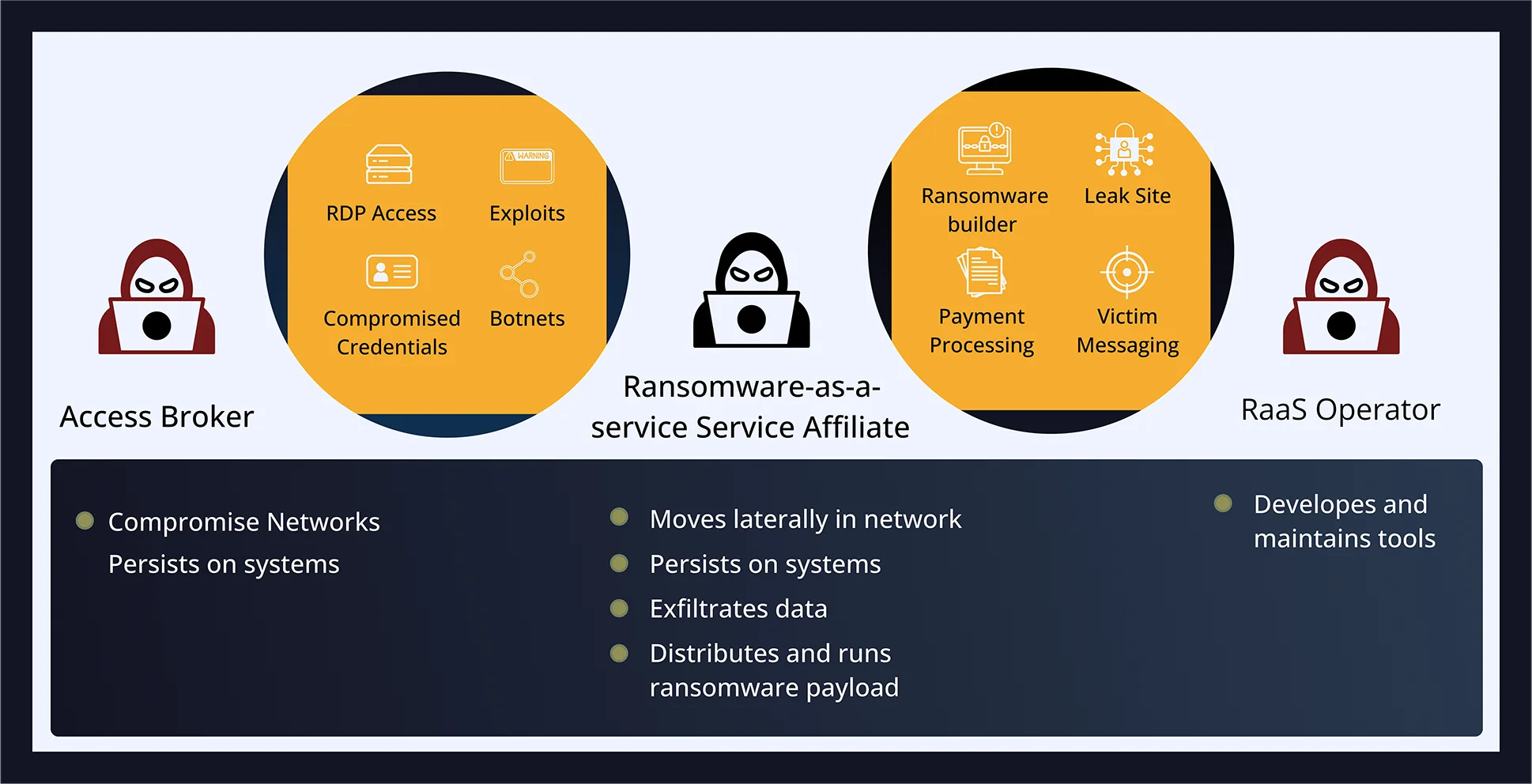
- Initial Access Brokers (IABs) sell access to unprotected systems
- Rust-written malware bypasses C/C++-focused signature tools
- Agentless endpoints (e.g., jump servers) become launch points
- Kerberoasting and credential theft enable trusted access
- Commands like net stop AV are used to disable AV/EDR
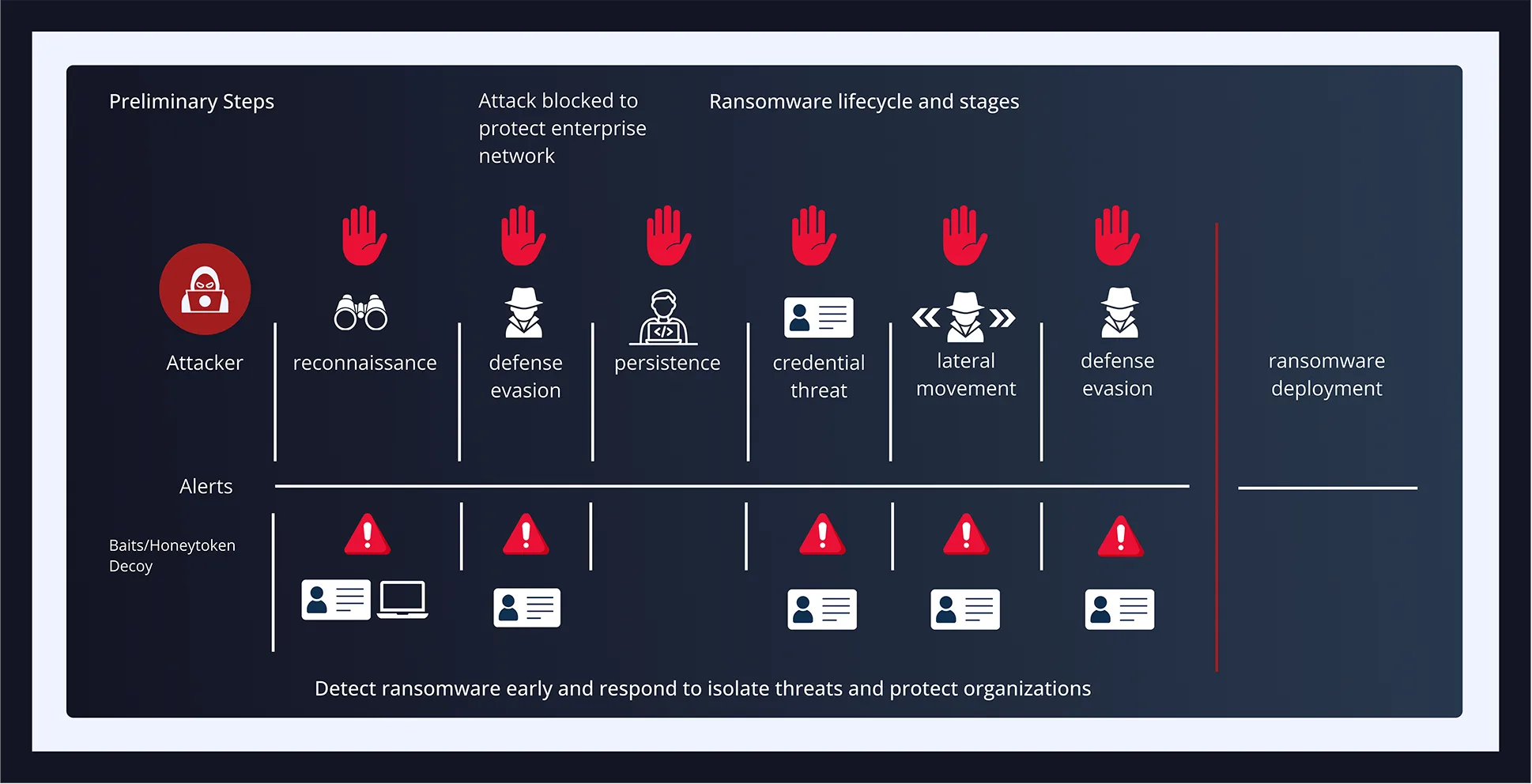
Detect Ransomware Across the Entire Attack Lifecycle
Ransomware is detected and blocked before it reaches the payload stage—regardless of the variant, toolset, or language used.
ShadowPlex deploys deception assets—honeytokens, breadcrumbs, and decoys—across identity, file systems, memory, and cloud workloads. These traps are strategically placed to detect attacker behavior from the moment they begin reconnaissance, through credential theft, lateral movement, and staging, all the way to just before encryption.
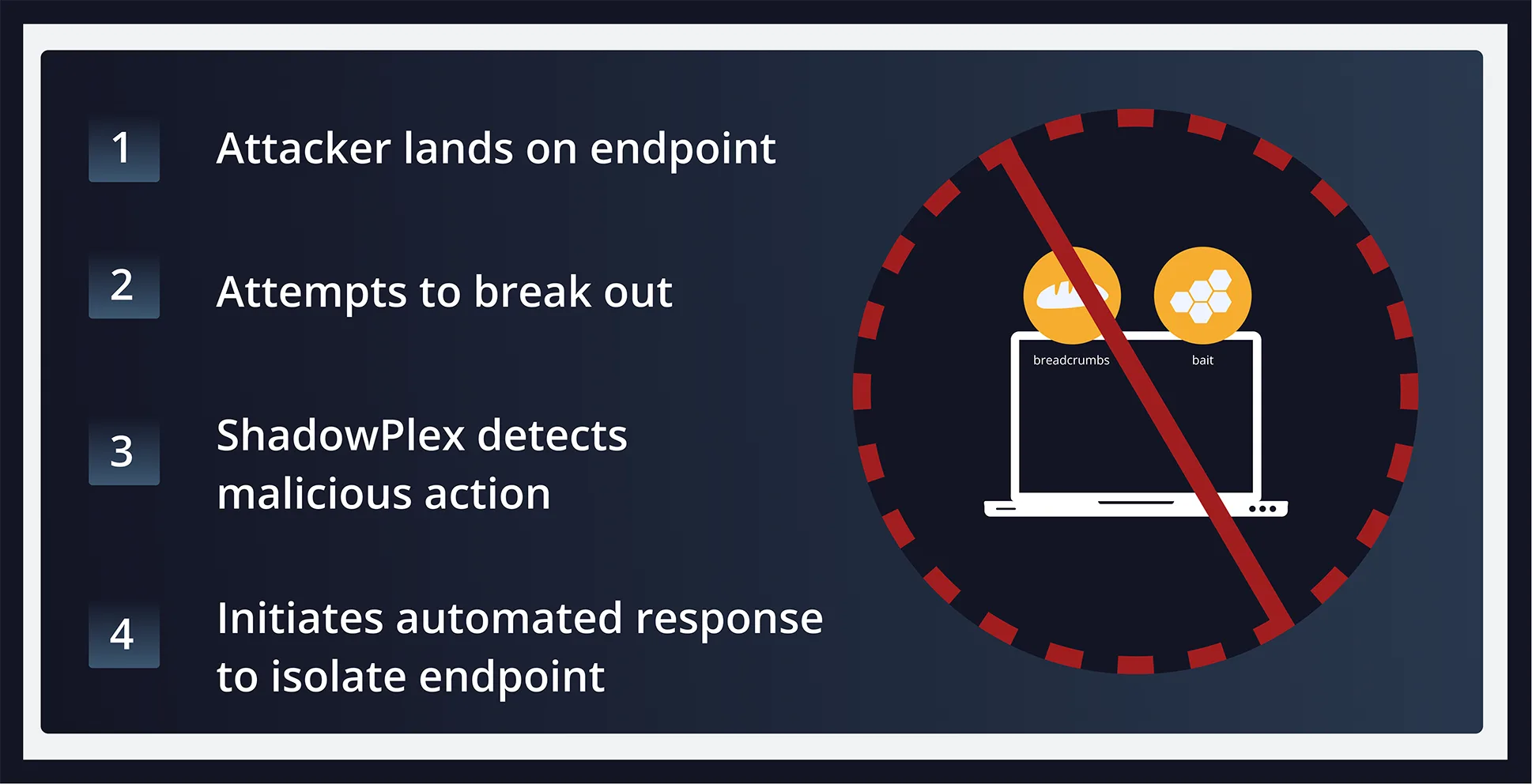
Trigger High-Fidelity Alerts and Automate Containment
Security teams don’t waste time chasing noise—response is immediate, automated, and based on real attacker engagement.
When ransomware interacts with a deceptive asset, ShadowPlex immediately triggers a verified alert. Prebuilt integrations with EDR, SOAR, and SIEM tools enable rapid policy-based isolation of compromised systems—stopping breakout activity in its tracks.
Built for Disrupting Ransomware. Focused on Preemptive Defense.
- Detect attacker behavior before payload deployment or encryption.
- Interrupt staging and escalation—without relying on indicators.
- Deception reveals intent-based activity that traditional tools miss.
- Gain coverage across identity, endpoint, and unmonitored infrastructure.
- Alert only on real ransomware engagement—not anomalies or noise.
- Automate containment through integrations with EDR, SOAR, and SIEM.
Frequently Asked Questions
Acalvio uses deception to detect ransomware based on behavior—not signatures or anomalies. It surfaces early-stage activity like credential misuse and lateral movement, before encryption or exfiltration begins.
Yes. ShadowPlex identifies attacker engagement with deceptive assets, regardless of ransomware language, signature, or delivery method—including Rust- and Go-based variants.
Absolutely. Acalvio covers jump servers, unmanaged endpoints, legacy infrastructure, and other agentless environments that are often blind spots for EDR.



