- Detect reconnaissance, credential misuse, and lateral movement early, strengthening defense validation.
- Provide verified alerts based on real Red Team behavior, eliminating noise and focusing investigation.
- Highlight gaps in identity, lateral movement, and access paths to guide defensive enhancements.
- Use Red Team engagement data to adapt defenses quickly—before real adversaries exploit the same pathways.
Acalvio Preemptive Defense Solutions Red and Purple Teaming
Tactics
- Reveals early-stage recon, credential misuse, and movement
- Surfaces tactics attackers would use in real-world breaches.
Validation
- Validates detection across IT, cloud, and OT attack surfaces.
- Supports continuous improvement with real attacker activity data.
Identity Attacks
- Detects credential theft and misuse before escalation occurs.
- Protects Active Directory and cloud identity paths from compromise.
& Privilege Escalation
- Exposes unauthorized movement across systems and domains.
- Detects privilege escalation attempts early before damage is done.
& Evasion Techniques
- Detects stealthy techniques like PsExec, RDP, and native tool abuse.
- Surfaces behavior traditional security often misses.
& Gap Closure
- Provides actionable insights to accelerate defensive tuning.
- Strengthens resilience after every exercise—before real incidents.

Surface real Red Team tactics early
- Detect early-stage reconnaissance targeting critical assets.
- Capture credential harvesting and password spraying activity.
- Identify lateral movement paths Red Teams exploit.
- Provide verified alerts during initial attack stages.

Validate detection and accelerate improvements
- Validate coverage across IT, cloud, and OT attack surfaces.
- Surface gaps traditional security tools miss.
- Adapt deception dynamically during exercises.
- Map detected activity to MITRE ATT&CK for clear action plans.

Detect identity-driven attacks before Red Teams escalate access.
- Detect credential theft early in the attack chain.
- Protect Active Directory and cloud identities from compromise.
- Surface service account abuse and lateral access attempts.
- Trigger alerts on unauthorized credential use.

Red Team escalation activities
- Detect unauthorized access to sensitive assets.
- Expose credential replay and privilege abuse.
- Surface lateral exploration across IT, cloud, and OT systems.
- Divert escalation attempts into deceptive environments.
Catch stealthy native tool use and evasive methods.
- Detect unauthorized PsExec, RDP, and PowerShell usage.
- Surface privilege escalation without reliance on signatures.
- Expose fileless attack techniques during exercises.
- Reveal hidden persistence attempts in IT and OT environments.

Every exercise tuned for operational resilience gains.
- Accelerate defensive tuning based on real attacker behavior.
- Prioritize fixes aligned to MITRE ATT&CK techniques.
- Improve detection coverage without operational disruption.
- Strengthen layered defense across identity, cloud, and OT environments.
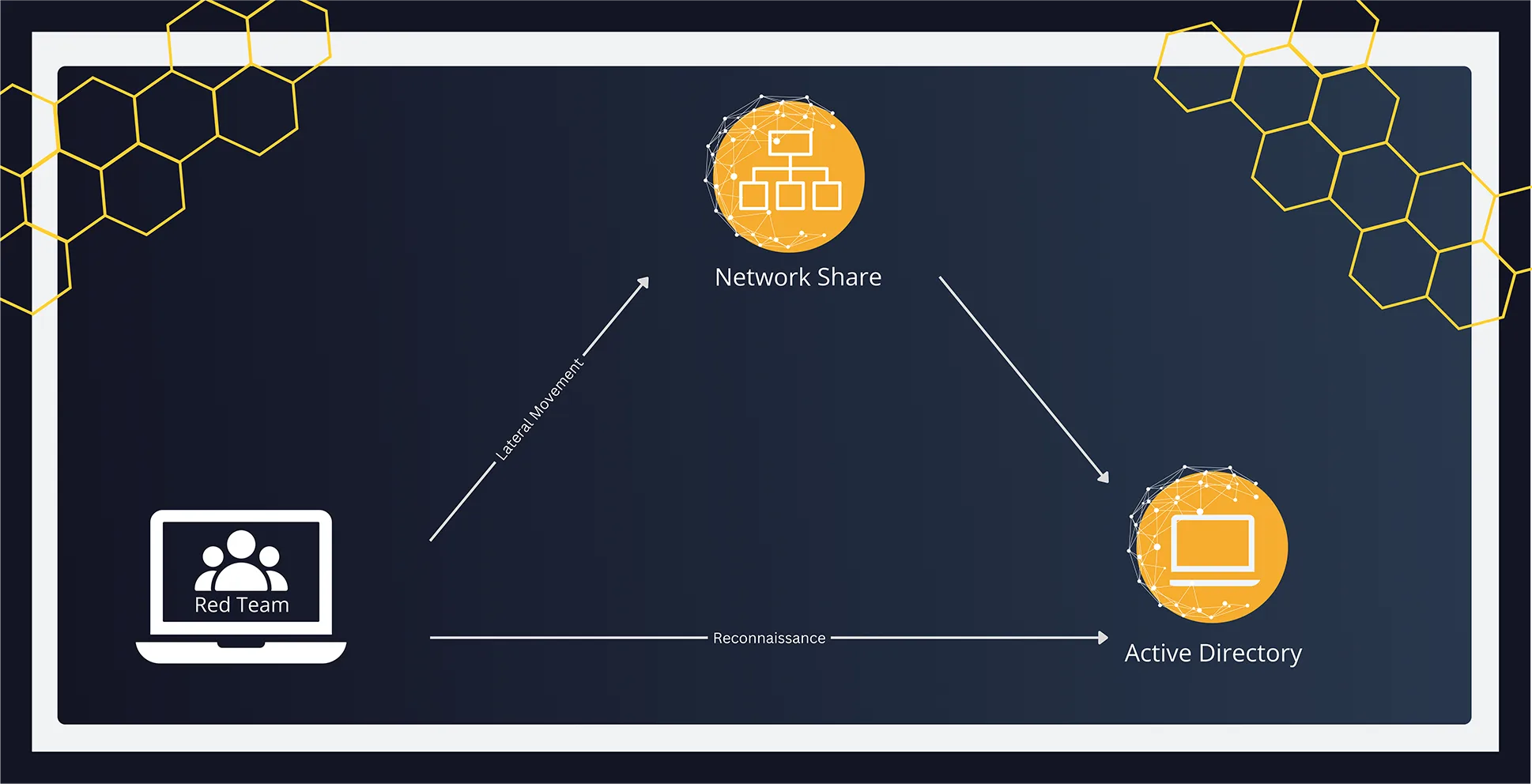
When a Red Team reaches critical assets like Active Directory without triggering alerts, it exposes serious gaps in early detection.
These gaps aren’t just exercise failures—they signal real-world vulnerabilities that adversaries could exploit if defenses aren’t strengthened.
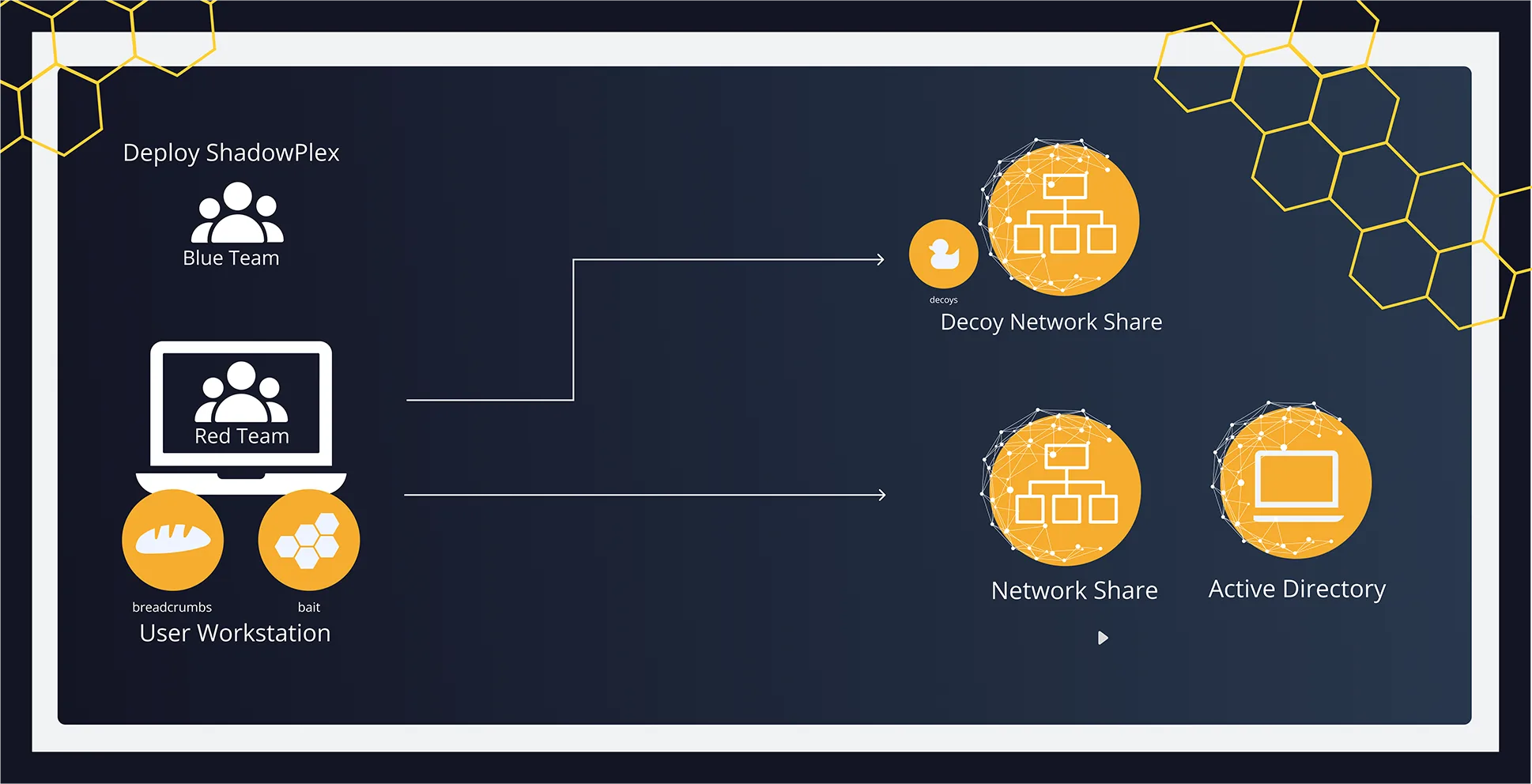
Strategic deception closes the detection gaps that Red Teams—and real adversaries—exploit.
By planting decoys, honeytokens, and baits across identity, cloud, and OT pathways, security teams gain early, actionable visibility into attacker behavior.
ShadowPlex gives security teams a decisive advantage in Red and Purple Team exercises by delivering early, high-fidelity detection without disrupting operations.
With ShadowPlex, you can:
- Detect Red Team tactics during reconnaissance, credential misuse, and lateral movement.
- Deploy deception across IT, cloud, and OT environments seamlessly.
- Trigger verified alerts based on real attacker engagement—not guesses.
- Strengthen defenses continuously with insights mapped to MITRE ATT&CK.
- Adapt deception dynamically during Purple Team exercises to validate improvements.
- Operate agentlessly without impacting production systems or exercise realism.
Built for Red and Purple Team Success. Focused on Preemptive Defense.
- Detect reconnaissance, credential misuse, and movement.
- Surface attacker behavior before objectives are reached.
- Turn Red and Purple Team insights into faster defense hardening.
- Strengthen IT, cloud, and OT defenses proactively.
- Trigger verified alerts from real attacker engagement.
- Deploy deception seamlessly without impacting operations.
Frequently Asked Questions
Deception surfaces real attacker behavior early—during reconnaissance, credential misuse, and lateral movement—giving security teams time to respond and strengthen defenses before objectives are reached.
No. ShadowPlex deploys agentlessly and operates invisibly. It detects attacker engagement without disrupting Red Team realism or impacting production systems.
Deception detects credential harvesting, lateral movement, privilege escalation, and Living-off-the-Land techniques like PsExec, RDP, and PowerShell that traditional tools often miss.



