- Detect attacker behavior with deception, not just IOCs.
- Surface credential misuse and lateral movement early.
- Focus investigations with early visibility into attacker behavior.
- Identify patterns and pathways without relying solely on logs or alerts.
- Investigate in-memory threats and process hollowing.
- Analyze PowerShell and scripts for covert behavior.
- Link deception with endpoint and identity telemetry.
- Validate hypotheses fast—without alert fatigue.

- Detect credential misuse, lateral movement, and privilege escalation attempts in real time—without waiting for alert thresholds or correlation.
- Reveal attacker behaviors that evade traditional tools, including Living-off-the-Land techniques and identity abuse.
- Uncover silent exploration in sensitive environments using decoys, breadcrumbs, and deceptive credentials.
- Uncover silent exploration in sensitive environments using decoys, breadcrumbs, and deceptive credentials.
- Trace adversary movement across IT, cloud, and identity layers by observing real attacker engagement with deception assets.
- Use similarity analysis to identify systems at risk based on shared traits with known compromised endpoints.
- Capture forensic artifacts from endpoints to identify attack TTPs and support faster investigation.
- Highlight likely attack paths to prioritize investigative focus and reduce dead-end analysis.

- Detect memory-resident threats, including process hollowing, DLL injection, and reflective loading techniques.
- Analyze PowerShell and other scripts for signs of obfuscation, credential access, and post-exploitation tools.
- Leverage deception to surface in-memory access attempts that bypass disk-based detection.
- Investigate runtime behavior with forensic depth—without relying on full system compromise.

- Link deception signals with endpoint, identity, and network telemetry to expose full attack sequences.
- Confirm hypotheses based on real attacker engagement—not inferred anomalies or weak signals.
- Cut through alert fatigue by filtering for intent-based behaviors that indicate active threats.
- Deliver high-confidence findings that accelerate response and guide mitigation efforts.
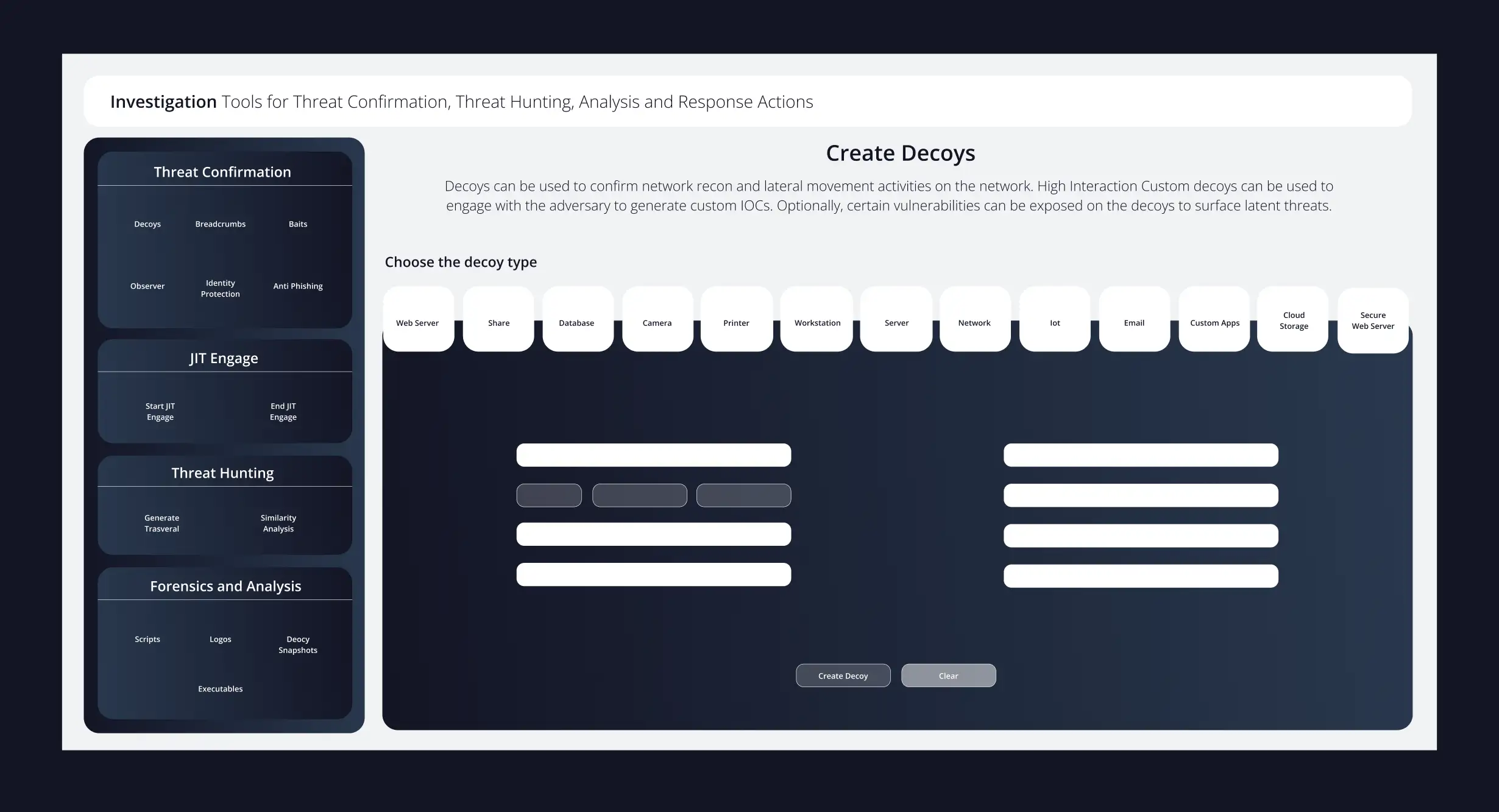
Acalvio Introduces Deception-Driven Threat Hunting
Traditional threat hunting relies on passive observation of attacker footprints. Acalvio adds a proactive layer by using deception to surface latent threats, confirm hypotheses, and accelerate investigations.
Key Capabilities:
- Dedicated Threat Hunting Workbench:Launch targeted hunts with preconfigured deception assets to expose hidden attacker activity.
- Controlled Deception Deployment: Deploy decoys and honeytokens strategically to draw out lateral movement, credential misuse, and privilege escalation.
- Active Hypothesis Testing: Use deception to validate hunting hypotheses, bringing an active engagement model to the threat hunting process.
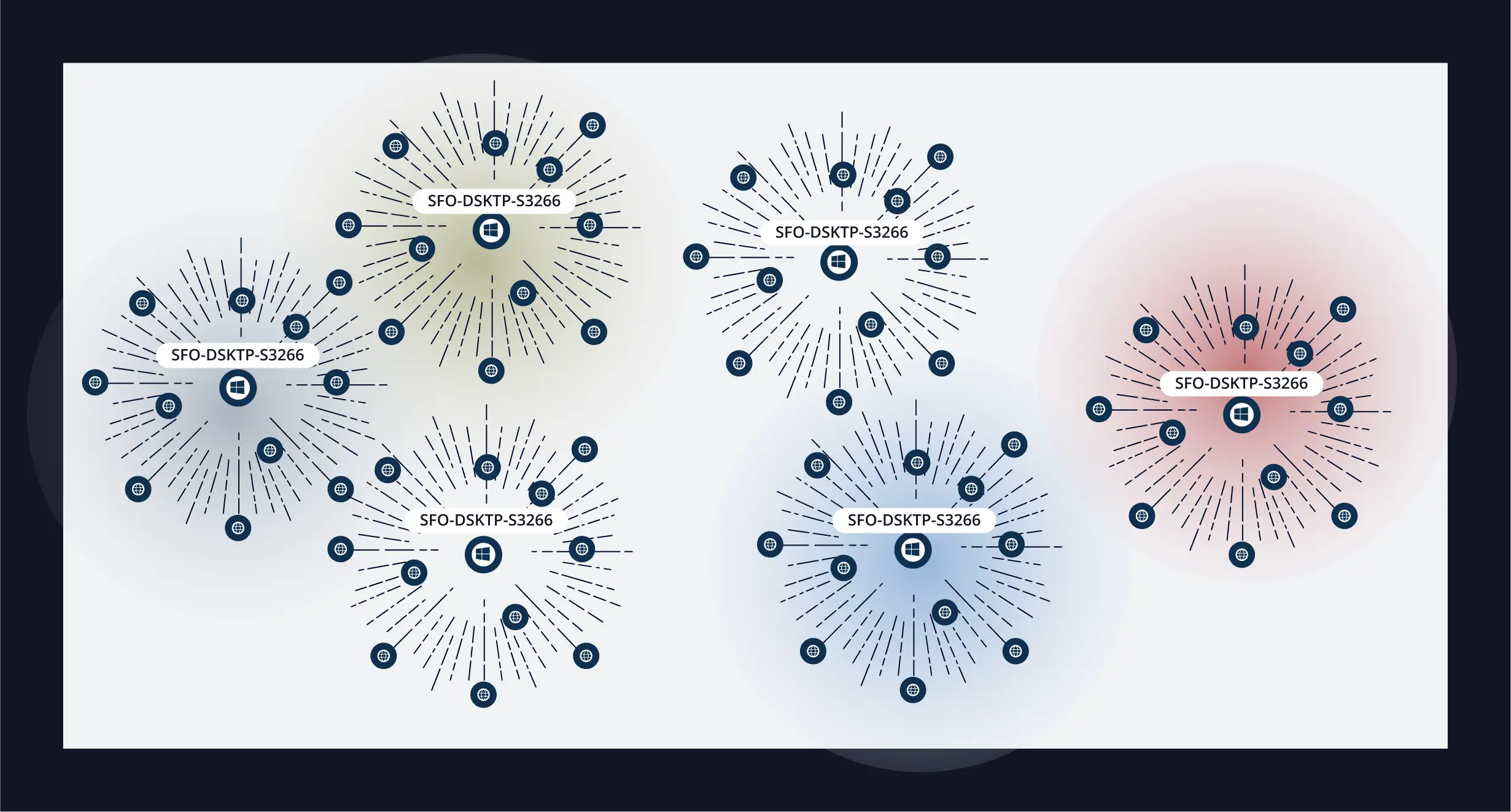
Adversary Traversal Mapping
It’s not just about finding activity; it’s about seeing how attackers navigate the network — hunters love path visibility.
- Map attacker movement across IT, cloud, and identity environments based on real deception triggers.
- Trace lateral movement and uncover paths to critical assets early.
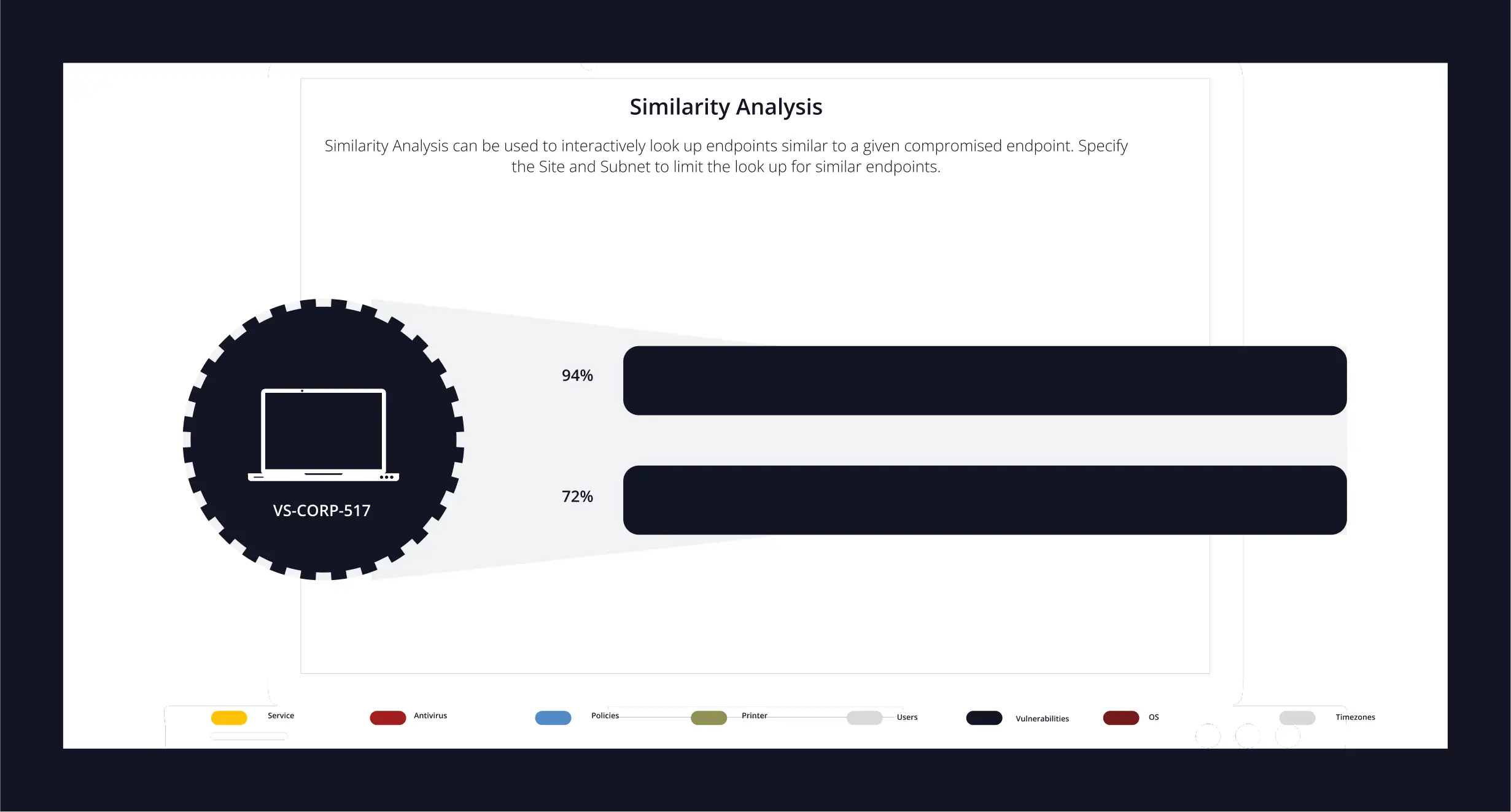
Link Analysis
Mature hunters think beyond the first compromised machine. They want to find the next 10 before it happens.
- Identify systems at risk by comparing traits of compromised endpoints.
- Expand hunt scope proactively without increasing false positives.
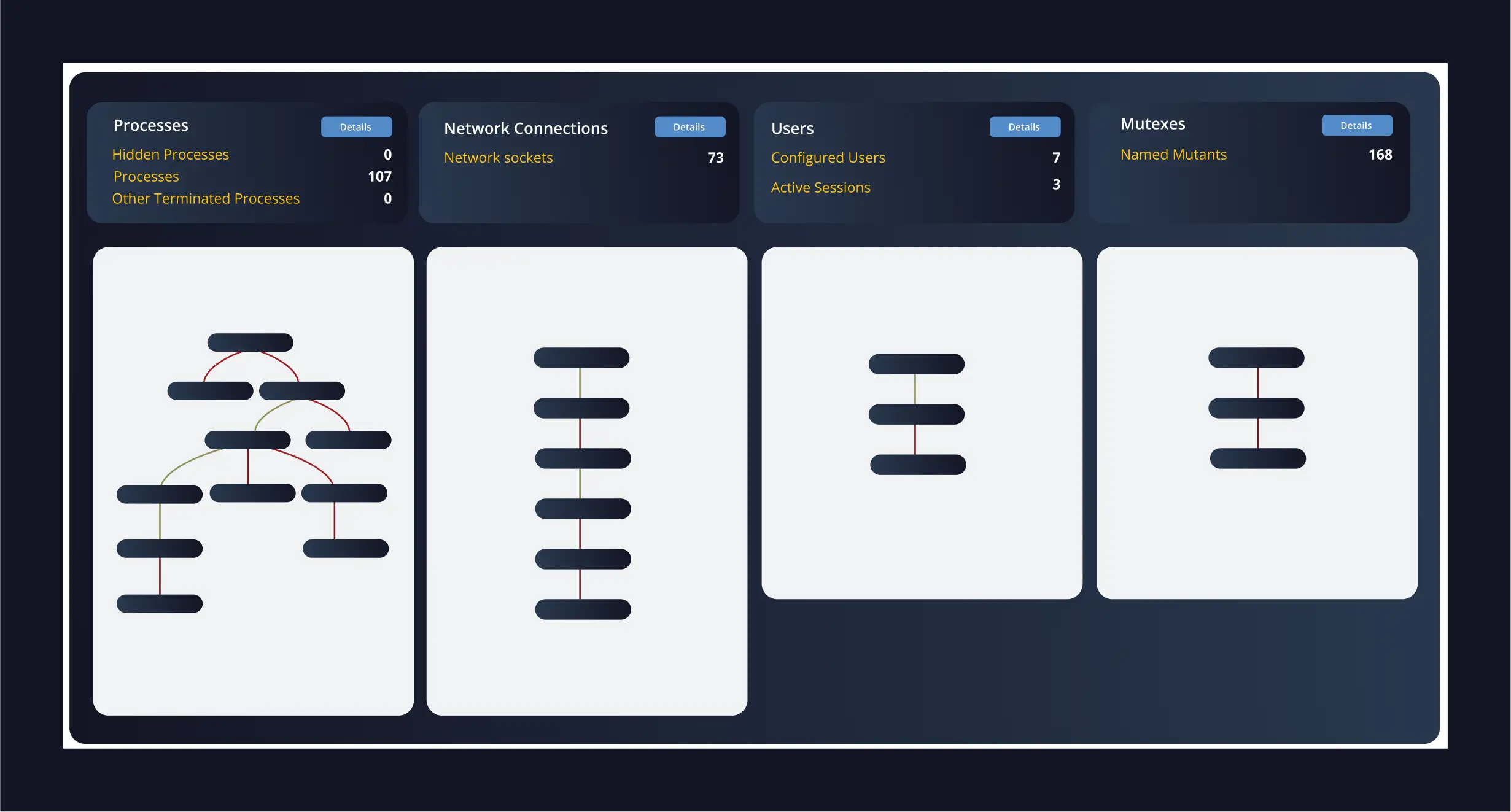
Advanced threats increasingly live in memory; if you can’t see memory, you’re blind to half the kill chain.
- Detect in-memory threats like process hollowing, DLL injection, and reflective loading.
- Investigate memory-resident attacks that bypass disk and EDR detection.
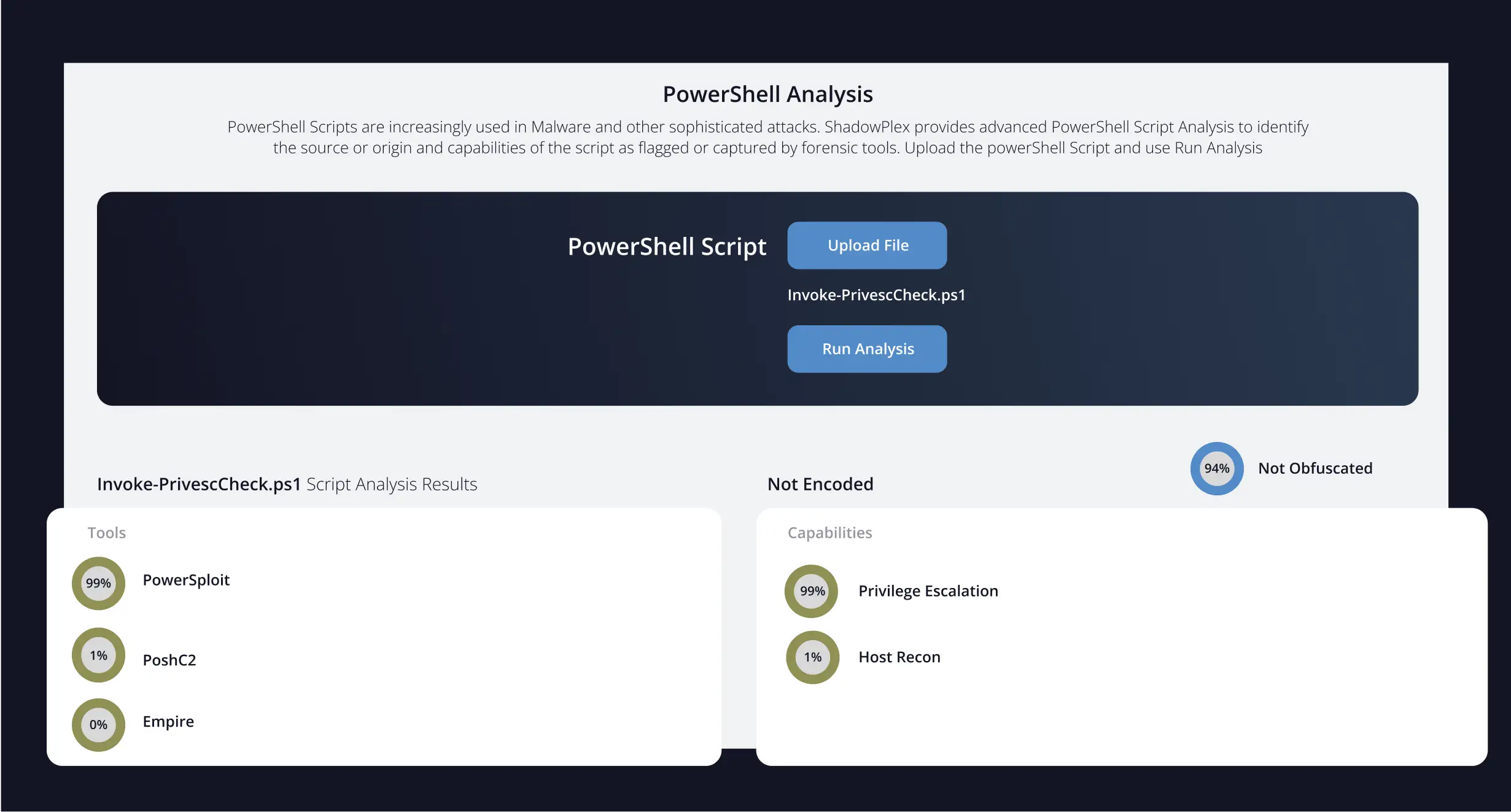
Many APTs use native scripts and obfuscated PowerShell. Threat hunters want native visibility here, not just IOC matching.
- Analyze PowerShell and script behavior for credential access, exfiltration, and persistence mechanisms.
- Uncover attacker intent and capabilities through runtime behavior inspection.
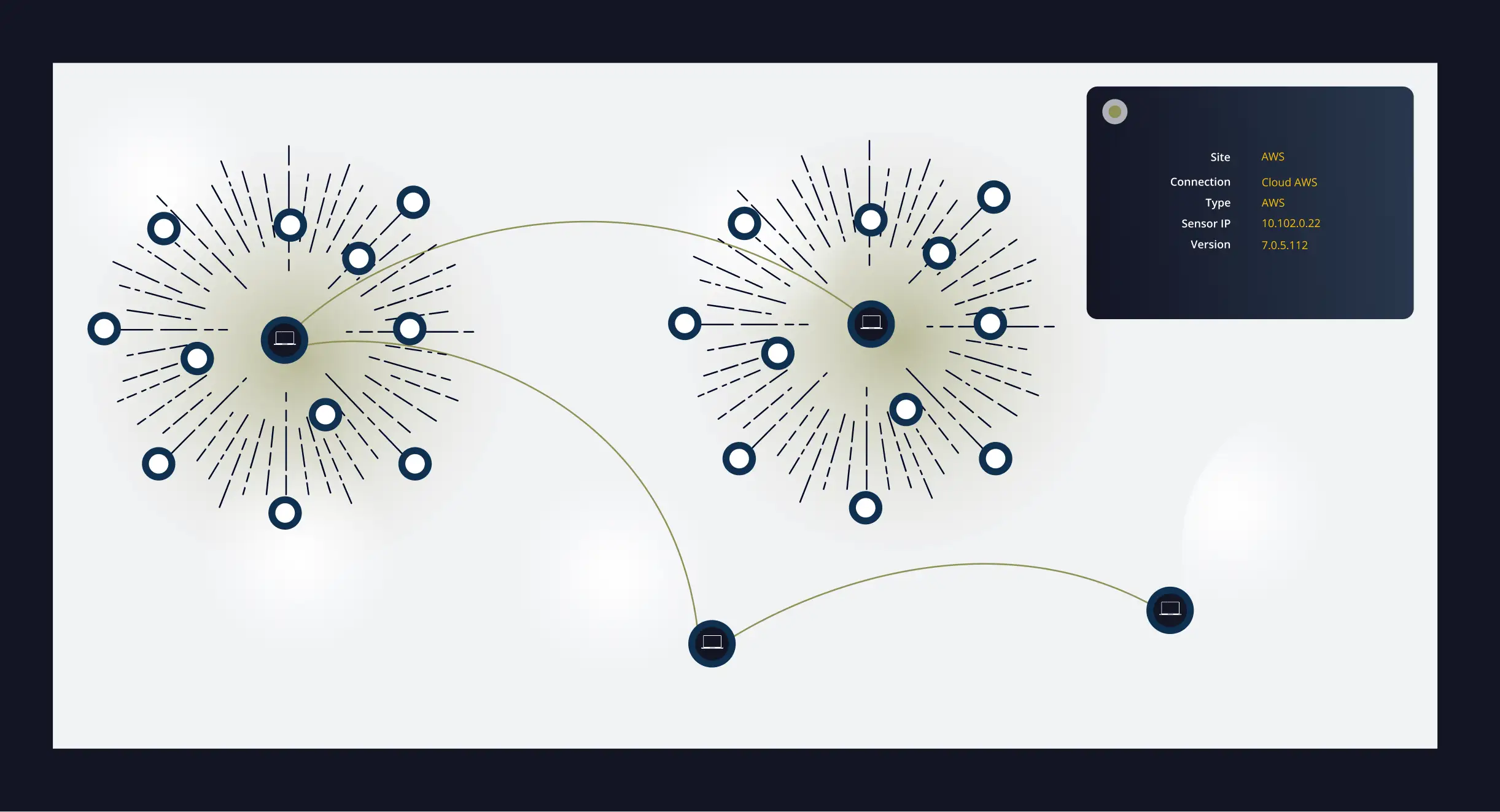
Hunters (especially Purple Teams) want to see progression, hypothesize, and test defensive coverage quickly.
- Correlate deception, endpoint, and identity data to reveal full attack sequences.
- Confirm adversary behavior and prioritize response based on real progression, not isolated events.
Frequently Asked Questions
Deception allows threat hunters to surface attacker behavior proactively—without waiting for IOCs or log triggers. Decoys, breadcrumbs, and baits reveal adversary movement as it happens, enabling early-stage investigation.
No. Acalvio enhances your existing hunting workflow by adding high-fidelity signals that reduce noise and accelerate hypothesis validation. It works alongside SIEMs, EDRs, and other data sources.
ShadowPlex surfaces stealthy techniques including credential misuse, lateral movement, in-memory malware, PowerShell abuse, and process hollowing—many of which are missed by traditional detection tools.



